Blogs and Resources

Security Advisory: July 2024 Microsoft Security Updates
Microsoft has released its July 2024 Patch Tuesday security updates, addressing a total of 143 vulnerabilities. This includes fixes for two vulnerabilities that are currently being actively exploited in the wild. The breakdown of the vulnerabilities includes five...
Security Advisory: July 2024 Microsoft Security Updates
Microsoft has released its July 2024 Patch Tuesday security updates, addressing a total of 143 vulnerabilities. This includes fixes for two...
Filter by

Difenda recognized as a finalist of 2024 Microsoft Americas Partner of the Year
Phoenix, AZ, USA — June 25, 2024 — Difenda, a full stack Microsoft Security services provider and winner of the 2023 Microsoft Canada Impact award, today announced it has been named a finalist for the 2024 Microsoft Americas Partner of the Year Award in Security. The...

Microsoft Security Insights Show: Advancements in AI-Driven Cyber Defense
Welcome to the world of cybersecurity, where innovations are fast-paced, and staying ahead of threats is a continuous challenge. Kyle Link and Andrew Hodges recently had the pleasure of speaking with the Microsoft Security team on the Microsoft Security Insights Show...

Difenda’s Threat Hunting Maturity Model
At Difenda, we've developed a comprehensive Threat Hunting Maturity Model (HMM) to help organizations evolve from basic reactive measures to advanced proactive threat hunting strategies. Let's explore the stages of our model and how each step helps build a more secure...

Security Advisory: High-Severity Vulnerability in SolarWinds Serv-U Exploited in the Wild
Difenda is issuing this advisory to inform all stakeholders about a high-severity vulnerability in SolarWinds Serv-U file transfer software, tracked as CVE-2024-28995. This vulnerability, which has a CVSS score of 8.6, allows attackers to read sensitive files on...

Understanding Modern Day Threat Actors
Over 17 billion personal records were exposed or stolen in 2023, understanding who these threat actors are and their motives is crucial for protecting your digital assets. What is a Threat Actor? A threat actor, also known as a malicious actor or adversary, is...

Security Advisory: June 2024 Microsoft Patch Tuesday Updates
Microsoft has released its June 2024 Patch Tuesday updates, addressing a total of 51 security vulnerabilities. Among these, 18 are remote code execution (RCE) flaws, and one is a publicly disclosed zero-day vulnerability, CVE-2023-50868, in the DNSSEC validation...

How Cyber Threat Intelligence Can Guide Threat Hunting – And Should.
In a not-so-distant past, in a bustling command center, the air was thick with the hum of powerful servers and the chatter of security analysts. It was a typical day until an urgent alert disrupted the routine. A known threat actor had struck again, but this...

Security Advisory: Urgent Update on Zero-Day Vulnerability CVE-2024-24919 in Check Point VPN Devices
On May 27, 2024, Check Point reported a significant spike in attacks targeting VPN devices. This activity was traced to a zero-day vulnerability, identified as CVE-2024-24919, affecting Check Point Security Gateways with remote access VPN or Mobile Access Software...

Proactive Cyber Threat Hunting: 3 Types of Threat Hunts Explained
One of the most effective ways to stay ahead of potential threats is through proactive threat hunting. This involves actively seeking out potential threats within your network before they can cause harm. There are three primary types of threat hunts that every...

Save Time on Threat Hunting with Microsoft Copilot for Security and Difenda
Microsoft Copilot for Security - simplified data analysis and streamlined threat hunt plans save SOC teams hours. In the ever-evolving landscape of cybersecurity, threat hunting has emerged as a proactive measure to identify and mitigate threats that have evaded...

Meet Our Expert Threat Hunter: Kyle Link
We are thrilled to introduce Kyle Link, the featured speaker for our upcoming webinar, "Inside our Command Center: a Live Look at Cyber Threat Hunting." Kyle is an Architect and expert threat hunter on Difenda’s Cyber Research & Response team, where he excels in...

Upcoming Webinar: Threat Hunt with Microsoft Copilot for Security
In today's rapidly evolving cybersecurity landscape, the need to stay ahead of threats has never been more critical. We are excited to announce our upcoming webinar, "Inside Our Command Center: A Live Look at Cyber Threat Hunting." This event is designed to provide...

Building a Business Case for Microsoft Copilot for Security: A Strategic Guide to Implementing Microsoft Copilot for Security
Building a Business Case for Microsoft Copilot for Security: A Strategic Guide to Implementing Microsoft Copilot for SecurityIntroduction: Who is This Guide For? This strategic guide is designed for IT leaders and decision-makers who are considering implementing...

Decoding Microsoft Security Copilot Pricing
How is Microsoft Security Copilot Priced? Microsoft Copilot for Security has a consumption-based pricing model determined by the number and complexity of prompts a business request. Pricing starts at $4 per provisioned Security Compute Unit (SCU) and is estimated to...

Security Advisory: Misuse of Microsoft Quick Assist by Storm-1811
Since mid-April 2024, the financially motivated cybercriminal group Storm-1811 has been observed exploiting the Microsoft Quick Assist tool in social engineering attacks. The group, known for deploying Black Basta ransomware, begins its attack chain with voice...

Security Advisory: Mitigating Threats from Black Basta Ransomware
The Black Basta ransomware has targeted over 500 organizations across North America, Europe, and Australia since April 2022, notably affecting critical infrastructure sectors. This ransomware-as-a-service operation employs a double-extortion tactic, encrypting and...

Podcast: Exploring Cybersecurity Strategy with Charter and Difenda
Strategic partnerships and technological innovation lead cybersecurity strategy advancements, creating resilient defenses against emerging threats. The Charter and Difenda collaboration showcases significant security posture improvements through strategic alliances...

Enhancing Cyber Security for Packaging Companies: A Case Study
Every phase of the packaging process is susceptible to potential breaches. Its heavy reliance on ICS, embedded computers, PCLs and SCADA systems throughout the production line makes it the perfect target. A leading manufacturing company recently transitioned to a...

Difenda wins 3 Cybersecurity Excellence Awards
We are thrilled to announce that Difenda has earned three prestigious awards at the 2024 Cybersecurity Excellence Awards, recognizing our commitment to innovation and leadership in the cybersecurity industry. Difenda has won the following awards during the 9th...

Enhancing Energy Security with 24/7 Security Monitoring and Security Automation
Energy companies face a variety of cybersecurity concerns due to the critical nature of their operations and the potential impact of disruptions. A large Canadian energy company, with operations across the globe and almost 2,500 employees, has partnered with Difenda...

Difenda Named Winner of 4 Global InfoSec Awards for the Fourth Consecutive Year
Difenda is excited to announce we have won four Global InfoSec Awards from Cyber Defense Magazine, the industry’s leading security magazine: Best Service MXDR Security, for Difenda MXDR, Most Innovative Operational Technology Security, for Difenda MXDR...

Infographic: LiUNA Pension Fund Trusts Difenda to Strengthen Security Posture

The 5 Phases of Remote Incident Response

Q&A: Bridging Data Protection and Security Operations with Microsoft Purview
In the recent webinar, we delved deep into the intricacies of blending information protection with security operations. As many of you have shown interest in practical applications of the strategies discussed, here are some of the most frequently asked questions...

Webinar Recap: Using Microsoft Purview to Bridge Information Protection and Security Operations
Our recent webinar, "Beyond Silos: Bridging Information Protection and Security Operations," co-hosted with industry leaders from Epiq Global, delved into how organizations can #PutSynergyInAction by merging data security and cybersecurity operations into a cohesive...

Pension Fund LiUNA Trusts Difenda to Strengthen Security Posture
Pension funds like the LiUNA Pension Fund face significant cybersecurity challenges as they manage large sums of money and sensitive member data. LiUNA Pension Fund, which oversees over $10 billion in assets for more than 142,000 members, has partnered with Difenda to...

Meet the Experts: Achieving Seamless Security Operations with Advanced Information Protection
As we gear up for our webinar, “Beyond Silos: Achieving Seamless Security Operations with Advanced Information Protection," we are thrilled to introduce you to our distinguished speakers, Andrew Hodges of Difenda and Jeremy Sawyer of Epiq. This event is your gateway...

Upcoming Webinar: Bridging SecOps and Data Protection with Microsoft Purview
Organizations are investing heavily in cutting-edge tools like Microsoft Purview and Microsoft Sentinel to fortify their defenses. However, this advanced arsenal often leads to an overwhelming influx of information protection alerts. Creating a unique challenge for...
Webinar Recap: Demystifying Cloud Security
In the dynamic landscape of cloud security, staying ahead means embracing innovative solutions that not only detect threats but also proactively mitigate them. This was the central theme of our latest webinar, which brought together experts from Difenda and Microsoft...

Navigating the Cloud: Insights from the Front Lines of Cloud Security
In a recent podcast, Difenda’s Chad Paquette sat down with Greg Wartes and Michael Vitale of Microsoft Security to discuss all things Cloud Security. Throughout their discussion, the group explored the critical importance of automatic triage in incident...

Difenda recognized as a Microsoft Security Excellence Awards finalist for Security MSSP of the Year
PHOENIX--(BUSINESS WIRE)--Difenda today announced it is a Security MSSP of the Year award finalist in the Microsoft Security Excellence Awards. The company was honored among a global field of industry leaders that demonstrated success across the security landscape...

Meet the the Demystifying Cloud Security Experts
As we gear up for our webinar, "Demystifying Cloud Security with Microsoft and Difenda," we are thrilled to introduce you to our esteemed speakers. Chad and Greg will be unravelling the intricacies of cloud security and sharing invaluable insights with our...

Sneak Peek: Difenda’s Microsoft Copilot for Security Custom Skills and Integrations
As part of Microsoft’s Copilot for Security Partner Private Preview, Difenda has had the opportunity to test and prototype multiple custom skills and integrations in the Copilot environment. As featured on our recent Copilot for Security Webinar, these skills and...

What is Microsoft Copilot for Security?
In the rapidly evolving digital landscape, cybersecurity has become a complex battleground against advanced threats and sophisticated cybercriminals. Traditional security measures are no longer sufficient to safeguard IT ecosystems, necessitating a shift towards more...

Microsoft Copilot for Security: Partner Private Preview Webinar Takeaways
Do you have highly repeatable security processes? What are the limitations between a junior analyst and a senior analyst? What are the responsibilities among them? How are you tracking KPI's between them? What are some workflows specific to your organization...

Upcoming Webinar on Demystifying Defender for Cloud: Everything You Need to Know
Cybersecurity trends indicate a shift in the attention of cybercriminals toward cloud environments. Microsoft's customer data shows that the number of organizations with four or more cloud workloads has increased by more than 40% yearly. In turn, as of 2024, 45% of...

Exploring Microsoft Copilot for Security: What You Need to Know Before the Webinar
The frequency and sophistication of cyber-attacks have improved drastically with access to generative AI tools. However, with the cybersecurity skills shortage still impacting the industry, the odds are against cyber-defenders. AI tools like Microsoft Copilot for...

Transform Your Digital Defense: Automated Cybersecurity with Microsoft Sentinel, Defender XDR and Difenda AIRO
Automated cybersecurity has become a fundamental operational process for safeguarding our digital environments. According to a study by Capgemini, over 63% of organizations state that AI has increased threat detection and response speed by at least 12%. The...

Maximizing SOC Efficiency with Security Automation in Microsoft Sentinel
The reliance on traditional, manual security monitoring methods is already outdated. Today the odds are against security teams. Over 4000 password attacks occur a second, 3.5 million cybersecurity jobs remain empty, and it only takes 72 minutes for...

Webinar on Microsoft Copilot for Security: Everything You Need to Know
4,000 password attacks occur per second, making the role of cybersecurity professionals even more crucial—and more challenging. But with an estimated 3.5 million unfilled cybersecurity positions, the industry is in desperate need of a champion. With AI emerging...

Webinar Recap: Securing OT: A Live Q&A for Cybersecurity Leaders
In a world increasingly reliant on interconnected systems, securing OT is of strategic importance. Our recent webinar, "Securing Operational Technology: A Live Q&A for Cybersecurity Leaders," focused exclusively on this critical arena, diverging from industries...

Securing Operational Technology Q&A: Managing OT Security Operations
In our latest informative webinar, we delved into the ever-critical topic of OT security operations. Our speakers, Kirsten Turnbull and Chase Applegate, shared their insights on numerous concerns and strategies relevant to OT security operations. Here's a recap of the...

Securing Operational Technology Q&A: Best Practices and Compliance
In our latest webinar, we delved into the ever-critical topic of Securing Operational Technology (OT) with cybersecurity. Our speakers, Kirsten Turnbull and Chase Applegate, shared their insights on numerous concerns and strategies for best practices and compliance...

Demystifying the Capabilities of Microsoft’s E5 for OT Security
You may have recently heard rumors that Microsoft Security added IoT capabilities to their E5 licensing structure. This is exciting because Defender for IoT has long been a separate licensing technology. With OT devices likely to double by 2030 this could have a large...

When IT and OT Security Converge: A Risk Management Approach
The convergence of IT and OT systems has ushered in an era of heightened efficiency and productivity. However, this integration has also introduced fresh security challenges. With historically separate and highly specialized systems now interconnected, vulnerabilities...

The Five Engines Powering OT Security Alerts
In today's world, technology is intertwined with nearly every aspect of our lives, and industrial operations is no exception. For cybersecurity leaders, understanding the key engines that monitor and detect Operational Technology (OT) security alerts is crucial. In...

Securing OT Environments: The Role of Security Automation in Threat Response
The line between inconspicuous routine actions and potential security threats is very thin. A mere click on an innocent-looking email can trigger a cascade of catastrophic events. For example, if an IT account gets compromised, and the breach escalates, it can...

Cybersecurity Gems from 2024 EDUCAUSE Top 10 Review
In a world where student populations are increasing, budget constraints are real, and classrooms are sprawling across geographical boundaries, cybersecurity in the education sector is a critical challenge. The 2024 EDUCAUSE Review places a spotlight on the necessity...

Unlock the Full Potential of Microsoft Sentinel with Difenda’s SIEM Optimization
Are you struggling with complex configuration, alert overload, cost management and a knowledge gap when it comes to Microsoft Sentinel? You’re not alone. Microsoft Sentinel is a cloud-native security information and event management (SIEM) platform that...

A Deep Dive into Microsoft Sentinel PoC with Difenda
Are you ready to fortify your cybersecurity defences and streamline your security operations? Look no further than Microsoft Sentinel. Microsoft Sentinel offers an all-in-one solution for threat detection, response, and remediation. With a PoC, you can see firsthand...

Difenda Selected For Microsoft Security Copilot Private Preview
Difenda today announced its participation in the Microsoft Security Copilot Partner Private Preview. Difenda was selected based on their proven experience with Microsoft Security technologies, willingness to explore and provide feedback on cutting-edge...

Unveiling The Power Of Microsoft Security And Difenda: Overcoming The “AllEggs In One Basket” Concern
In today's digital landscape, where cyber threats are ever-evolving and becoming increasingly sophisticated, robust cybersecurity measures are paramount. Microsoft Security, an all-in-one, end-to-end cybersecurity technology suite, has overcome the narrative of not...

Difenda’s 14-Step Microsoft Sentinel Migration Process
Discover Your Migration Journey! You Shouldn't Have To Pay More For SIEM Automation And UEBA. With Microsoft Sentinel, you get everything you need out of the box. Discover what your migration journey will look like.Our 14-stage process allows you to: - Utilize Your...

Planning Your Splunk To Sentinel Migration: The 9-Point Migration Checklist
Planning a Splunk To Sentinel Migration is a strategic decision that optimizes your existing infrastructure investments. However, it's no small task and requires meticulous preparation. This is your roadmap for planning your migration from Splunk to Microsoft...

Maximizing Microsoft Security With Microsoft And Difenda: A Webinar Recap
In a rapidly evolving digital landscape, organizations face constant cybersecurity threats that can jeopardize sensitive data and operations. Fortunately, Microsoft offers a suite of powerful security solutions to help protect your organization. In a recent webinar,...

Webinar: Maximizing On Microsoft Security With Microsoft And Difenda
Get On-Demand Access to the Webinar Recording! See How Difenda Works In Your Environment. Learn how to harness the full value of your Microsoft license See the power of the Microsoft Defender Suite Test Microsoft Sentinel automation Discover strategies to gain...

Difenda Is Recognized As A Top 250 MSSP For The Third Year In A Row
Difenda is a top 100 MSSP on the Top 250 MSSPs 2023 list by MSSP Alert, a CyberRisk Alliance resource. In the fast-paced world of cybersecurity, consistency is key. For the third consecutive year, Difenda has proven its unwavering dedication to excellence in...

Maximizing Microsoft Threat Intelligence Capabilities With Difenda Threat Profiling
Effective threat mitigation requires a deep understanding of the threat landscape and the context in which alerts occur. By analyzing and categorizing assets within the organization's environment, cyber threat profiling offers insights into the potential impact of...

Glossary of Cybersecurity Terms in Higher Education
In the ever-evolving landscape of digital threats, Cybersecurity in Higher Education stands as a critical area of focus, demanding attention and understanding from educators, administrators, and IT professionals alike. This glossary serves as a foundational guide,...

Enhancing Email Security in Education: A Comprehensive Guide to Managed Email Security Services and Microsoft Defender for Office 365
In today's digital age, email remains a critical communication tool in educational institutions. However, it's also a common target for cyber threats like phishing, spear phishing, and other forms of email-based attacks. Managed Email Security for Education,...

Achieving Proactive Cybersecurity: A Guide for Executives
In an era where cyber threats are evolving at an unprecedented pace, achieving cybersecurity readiness has become a top priority. Shockingly, only 37% of businesses report feeling “confident that their company was properly secured against a cyber-attack. Moving beyond...

Strengthening Your Security Posture with Data Governance
Leveraging Microsoft Purview for Unified Cybersecurity Excellence Data has become the new currency of digital transformation, offering unprecedented opportunities for insights and improved decision-making. However, as the volume, velocity, and variety of data...

Innovation and The Current Threat Landscape
Navigating the Complex Threat Landscape of Cybersecurity in an Era of Innovation Imagine, a dynamic tech company on the cusp of a groundbreaking IoT device launch. Amidst excitement and innovation, they experience a cyberattack exploiting a vulnerability in...

Difenda’s Microsoft Advanced Specializations & Your Security Solutions – 2023
Difenda is among the first Microsoft Partners to earn both the Microsoft Cloud Security Advanced Specialization and Microsoft Threat Protection Advanced Specialization When looking for new ways to protect and monitor the security of your IP and customer...

What are the Key Benefits of a Security Operations Center? SOC Benefits Explained
A security operations center (SOC), managed or in-house, can help mitigate the risk of a data breach occurring and limit risk when a breach occurs. But the role of a SOC and its business benefits go far beyond just that. In this post you will learn what a...

Video: Difenda and Microsoft Join Forces to Reduce Alerts for the City of Brampton
Facing a dynamic threat landscape, The City of Brampton partnered with Difenda to streamline its security tools into a unified suite powered by Microsoft Sentinel, Defender for Office 365, Endpoint, and Cloud Apps. This consolidated approach bolstered protection...

Securing A Safe Learning Environment in 2023 and Beyond

Microsoft Inspire 2023 Recap: Unveiling the Future of Technology and Innovation
Microsoft Inspire 2023 showcased a future where innovation and artificial intelligence intersect to revolutionize how we work and enhance cybersecurity. Among the highlights, Copilot emerged as a game-changer, promising to transform various aspects of our daily...

Celebrating Three Consecutive Years as a Great Place to Work® in Canada!
At Difenda, we believe that a great workplace is not just about the products or services we offer, but also about the people who make it all possible. We are thrilled to announce that Difenda has been re-certified as a Great Place to Work® in Canada for the third...

Creating Cyber Resilience in Brampton with Microsoft Security & Difenda
Defending a Vibrant City with Cutting-Edge Cybersecurity Solutions As the ninth most populous municipality in Canada, the City of Brampton faces an ever-evolving threat landscape in maintaining the safety and security of its nearly 700,000 citizens. To address...

Implementing a Robust Cybersecurity Framework in Education: A Case Study from a Leading Toronto College
In an era where cybersecurity is paramount, educational institutions are increasingly finding themselves at the crossroads of digital vulnerability and the need for robust protection. A leading Toronto college recently embarked on a transformative journey to overhaul...

How Difenda’s Customer-Centric Solutions Earned Them the 2023 Microsoft Canada Security Impact Award
Difenda is proud to announce it has won the 2023 Microsoft Canada Security Impact Award. These annual Canadian awards recognize the Microsoft partners who have enhanced the lives of Canadians by championing diversity and inclusion, providing exceptional customer...

MSSP Technical Requirements for Cybersecurity In Education: What You Need to Know
In today's digital age, organizations face an ever-increasing number of cybersecurity threats. As such, it's essential to have a robust security infrastructure in place to protect your company's sensitive data and assets. One-way organizations can bolster their...

April Build Partner Champion 2023
We are thrilled to introduce Jonathan Raymond, Cybersecurity Executive- Ontario Public Sector at Microsoft and the proud recipient of the April Build Partner Champion award. Jonathan has consistently demonstrated commitment to Difenda and Microsoft's...

The 10-Point Cyber Security RFP Checklist
When selecting a Managed Security Service Provider (MSSP) through a Request for Proposal (RFP) process, how can educational institutions ensure they select the right MSSP to meet their cybersecurity needs? In this blog post, we'll guide you through our 10-point...

The Growing Threat Of AI-Driven Phishing Attacks
Artificial intelligence is one of the hottest topics in the industry right now, whether that is about ChatGPT, improved operations or advancing technologies there is a lot of buzz around AI. One serious implication of the commoditization of AI is malicious misuse of...

Webinar Recap: SecurED With Microsoft And Difenda
In a recent webinar, Difenda's cybersecurity experts teamed up with Microsoft Security to discuss how you can overcome common cybersecurity challenges in the education sector and understand what is possible with your licensing capabilities. They covered the...

Webinar: SecurED: Creating A Safer Learning Environment In The Cloud
Get On-Demand Access to the Webinar Recording! Download a copy of the Buyer's Guide Here. SecurED: Creating A Safer Learning Environment In The Cloud With The Microsoft Defender Ecosystem In response to the increasing demand for regulatory compliance and...

A Buyer’s Guide: Managed Microsoft Security Services in Education
Access The Guide! Uncover The 6 Major Red Flags To Avoid When Selecting An MXDR Provider For Education In A Buyer's Guide For The Education Sector, you will also learn: The top 5 things you must look for in an MXDR provider. 3 current trends in the industry...

How to Maximize Your Microsoft Security 365 A5 Investment
In today's digital age, cybersecurity threats continue to increase in sophistication and frequency. Educational institutions are not immune to these threats and actually take on over 68% of all malware threats. They must take proactive measures to safeguard their...

Case Study: Creating A Safer Learning Environment With MXDR
Customer Situation A higher education organization had limited resources and budget to invest in cybersecurity. The company had legacy technology in place, and the biggest challenge was that their team was so overwhelmed by the number of tools and products they had....

White Paper: Microsoft Cybersecurity for Education
Access The White Paper! Cyberattacks In The Education Sector Grew By 17% Last Quarter Are you worried about the security of your Educational Institution's sensitive data? Do you want to ensure that your network and endpoints are protected from cyber threats and...

Securing A Safe Learning Environment in 2023 and Beyond
In today's digital age, Educational Institutions are increasingly reliant on technology to support learning and administrative functions. As the education networks continue to expand the risk of security incidents only grows. Unfortunately, the sensitive nature of the...

XDR vs EDR – Key Differences Explained
Choosing between XDR and EDR can significantly impact your organization's cybersecurity. Our guide simplifies this decision, offering a clear comparison of Extended Detection and Response (XDR) versus Endpoint Detection and Response (EDR). Whether you're an IT expert...

Understanding the Cyber Risks To Educational Institutions and How to Mitigate Them
In recent years, educational institutions have become a prime target for threat actors looking to exploit weaknesses in their cybersecurity strategies. From K-12 schools to colleges and universities, educational institutions of all types and sizes have been targeted...

How a Law Firm Improved Their Security Posture with Data Governance and Compliance
The Challenge This large law firm faced challenges in managing and protecting sensitive data across its various offices. With strict regulatory requirements and frequent cybersecurity threats, they were on a mission to improve their security posture and make...

Difenda Build Partner Champion Q2, 2023
How Sycomp And Difenda Are Winning Together https://vimeo.com/user138416541/build-partner-champion-q2-2023?share=copy In this quarter's Build Partner Champion video, we're celebrating Global Accounts Manager, Tyler Fanning of Sycomp. In this video, he discusses the...

For the Third Consecutive Year: Difenda Wins Four Global InfoSec Awards
Difenda Wins ' Market Leader Microsoft Security Professional Services', ' Editor's Choice Managed Extended Detection and Response (MxDR)', ‘Cutting Edge OT Security' and ' Next Gen Vulnerability Management as a Service' at the 11th Annual Global InfoSec Awards...

College Blocks Business Email Compromise with Managed Email TDR
Challenge A higher education organization had limited resources and budget to invest in cybersecurity. The company had legacy technology in place, and the biggest challenge was that their team was so overwhelmed by the number of tools and products they had. Like many...

Elevate Your Compliance Strategy with Difenda’s Microsoft Purview Consulting Services
Introduction: In today's fast-paced and highly regulated financial services sector, maintaining compliance with industry standards and regulations is not just a necessity; it's a strategic advantage. Many companies, operate at the intersection of innovation and...

Difenda Build Partner Champion Q1, 2023
Scott Shimp of Microsoft is Difenda's Q1, 2023 Partner Champion! Over the past few years, Scott has shown us the value of collaboration, trust and consistency. His dedication to finding the right solution for his customers with Microsoft and Difenda solutions...

Top 3 Tips for Cybersecurity in Finance
The recent advances in internet banking such as mobile banking, instant payments and payment apps all invariably increase the finance industry's attack landscape and introduce new vulnerabilities. With the exponential growth of malicious acts by cybercriminals,...

Consolidation & Simplification: The Future Of Cybersecurity Management
Access The White Paper! Is Your Cybersecurity Team Struggling With Complex And Overlapping Security Technologies? This white paper, written by the Difenda security team, will guide you through security consolidation and...

A Manufacturer’s Guide To Understanding OT Security
Download The Guide! A Manufacturer's Guide To Understanding OT Security For two years the world has been talking about how to secure the OT environment. Now's the time to stop talking and do something. In this guide you'll learn: The top 3 threats to the...

Difenda recognized as a Microsoft Security Excellence Awards finalist
Difenda today announced it is a Security Service Innovator and Diversity in Security award finalist in the Microsoft Security Excellence Awards. The company was honored among a global field of industry leaders that demonstrated success across the security...

Video: Security Simplification and Consolidation
https://vimeo.com/user138416541/security-simplification-consolidation

The Ultimate Guide to Treating Ransomware Breach Face
Let Us Fix Your Face! The Ultimate Guide to Treating Ransomware Breach Face Shocked by accidentally causing a cyber breach within their company, employees everywhere are causing damage to their faces - until now. Follow these proven steps and let Difenda help fix your...

What is Ransomware Breach Face?
Ransomware Breach Face happens to people who unintentionally appear surprised, shocked, saddened, or frightened when they accidentally cause a cyber breach within their company. Basically, it happens when you accidentally click on a phishing email or receive a...

Using SIEM To Detect Ransomware Attacks
The goal of SIEM technology is to identify potential security threats and suspicious activity that can lead to cyberattacks such as Ransomware. In the case of a ransomware attack, SIEM can detect malicious activity, such as unusual file access or modification,...

Case Study: Treating Ransomware Breach Face with Difenda MXDR
In recent times, ransomware attacks have become a major concern for organizations of all sizes. The threat of exposure to malicious attacks has become more prominent and can lead to serious consequences. For one business that is exactly what happened. In...

Is Your MSSP Doing Everything They Can to Treat Ransomware Breach Face?
Thousands of businesses are affected by ransomware attacks every day. According to a recent report by Cybersecurity Ventures, ransomware attacks are projected to cost businesses $11.5 billion in 2023, up from $325 million in 2015. This indicates a significant...

Approaching Cybersecurity in the Manufacturing Industry
The manufacturing industry is under constant attack from cyber criminals looking to steal sensitive data and intellectual property, disrupt production processes, or compromise critical infrastructure. But, approaching cybersecurity in the manufacturing industry can be...

What Are The Benefits of MXDR for OT?
In an increasingly digital world, MXDR for OT is a critical tool for organizations looking to ensure the continuity of operations. OT systems are critical to the production process, and any security breach can have a significant impact on the...

Top three tips for cybersecurity in Manufacturing
Cybersecurity in the manufacturing industry is becoming increasingly critical as companies rely more on technology and interconnected systems to drive efficiency, productivity and innovation. The industry has seen a surge in cyber-attacks and data...

How to Measure the Success of Your MXDR for OT Security Program
Operational Technology (OT) cybersecurity is crucial for ensuring the reliability and security of industrial control systems and other critical infrastructure. As such, measuring the success of OT security ensures that businesses are effectively protecting their...

Protecting Intellectual Property at the Factory Level
The manufacturing industry has been greatly impacted by the rise of digital technologies. As production processes become increasingly digitized and connected, the importance of cybersecurity in the manufacturing sector has become increasingly evident. The...

The Integration of IT and OT Security
Information technology (IT) and operational technology (OT) cybersecurity protection are two distinct fields of cybersecurity, each with their own unique set of challenges and requirements. The main difference between IT and OT cybersecurity protection is...

Difenda Build is Celebrating One Year of New Partner Relationships
2022 was a big year for Difenda in many ways. At the beginning of the year, we launched Difenda Build, our channel partner program, with the goal of supporting more customers, providing continued value to our current partners, and extending the power of the Difenda...

Difenda MXDR for OT VS. The Other Guys
Difenda MXDR for OT (Managed Extended Detection and Response Operational Technology) is a cybersecurity solution that provides a unique approach to protecting industrial control systems (ICS), supervisory control and data acquisition (SCADA) systems, and programmable...

Difenda Build Partner Champion 2022
As the first Build Partner Champion, Jordan Herman of Softchoice has shown us the value of determination and collaboration. Difenda's Build Partner Champion award recognizes a partner team member who has made a tremendous impact on our joint customers....

Understanding MXDR for OT
Managed Extended Detection and Response (MXDR) for Operational Technology (OT) is a cybersecurity solution designed to protect industrial control systems and critical infrastructure from cyber threats. MXDR for OT is a critical aspect of security where the...

OT Environment Assessment Report
Download The Assessment! Sample OT Environment Assessment Report With Difenda MXDR for OT, you get a detailed summary of the potential security threats in your organization's OT environment right now. This detailed report: - Highlights vulnerabilities in your...

Invero and Difenda Partner for Seamless Cloud Solutions
Invero and Difenda have announced a strategic partnership to provide end-to-end cloud and security services, exclusive to the Microsoft portfolio. "These days, security is all about consolidation- and that bleeds into the sales process as well. You can no...
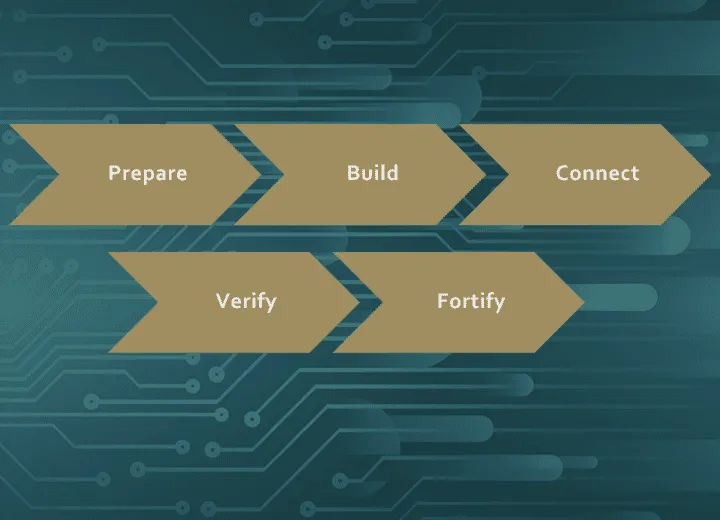
Difenda MXDR Deployment Process
Protection by the Difenda Shield starts quickly with our proven 5- step methodology. Difenda MXDR deployment leverages automation to simplify and expedite onboarding - a process which typically takes 6 to 8 weeks. Prepare Successful projects follow a plan....

What are the Benefits of MXDR?
MXDR allows organizations of all sizes to benefit from a world-class cybersecurity program. It broadens the scope of security while breaking through visibility barriers by integrating protection across an organization's endpoints, servers, cloud...

What is Microsoft Managed XDR (MXDR)?
Today, 67% of security leaders feel overwhelmed by the evolving threat landscape. Managed XDR is a proactive, efficient solution to gaining visibility into the security environment and stopping threats before they can affect your...

Whitepaper: Public Key Infrastructure
By now, the story of the Kaseya ransomware attack is a cautionary tale to all MSP's and their clients. However, Public Key Infrastructure (PKI) has become an integral component within business services and IT infrastructure. PKI provides trusted items that establish...

Whitepaper: Why Having the Right Penetration Testing Strategy Matters More Than Ever
Young african male programmer writing program code sitting at the workplace with three monitors in the office. Image focused on the screen

Difenda MXDR – Now Microsoft Verified
As of January 2023, Difenda achieved Microsoft verified Managed Extended Detection and Response (MXDR) solution status. The verification will enable Difenda to deliver next-generation security solutions to clients, further increasing the level of protection. It...

How Difenda MXDR integrates with Microsoft Security Technology
Difenda MXDR (Managed Extended Detection and Response) minimizes the gap between speed of compromise and speed of detection with proactive threat hunting and incident response services. Utilizing machine learning and analytics, Difenda MXDR correlates activity,...

Case Study: Architecting Security Environments for Unique Hybrid-Cloud Networks
Challenge This large media organization has a complex multi-cloud environment comprised of a corporate IT network and a public-facing product network that is continuously changing. They were struggling to manage multiple tools as their extremely complex environment...

2022: The Year We Changed The Game
2022 was a big year for Difenda. Not only for our team but for our partners and customers who put their trust in us to protect their businesses. At every step of the way, we ensure that the needs of our customers are heard and we always deliver. We...

Webinar: Change The Game With KQL Level 2
Get On-Demand Access to the Workshop Recording! Download a copy of the KQL workbook here.

Microsoft KQL Workbook
Get Your Microsoft KQL Workbook! Get on-demand access to the Workshop recording here. Change The Game With KQL Level 2 Workbook Elevate your ability to deliver on enhanced Sentinel queries by taking your Microsoft KQL skills to the next level - Learn how, when and why...

More MSPs are Becoming MSSPs; Which Should You Choose?
For security leaders, the cybersecurity of your business and the data of your customers is of the utmost importance. You know that it is critical to work with security service providers you can trust. But with MSPs making changes to their service offerings...

Why Consolidation Should be Your #1 Cybersecurity Priority in 2023
Organizations today are overwhelmed with choices when it comes to security tools and technologies. In 2019, the average business had 75 security tools in its environment. As organizations continue to rapidly adopt emerging security technologies, they...

Cybersecurity Planning 2023 Q&A
Cybersecurity is a fast-evolving sector and likely what you planned for last year won't work for 2023. As security and risk management leaders handle the recovery and renewal phases from the past two years and begin cybersecurity planning for 2023, they...

What Is Endpoint Detection and Response? EDR Security Deep Dive
Right now, many businesses are playing catch up with endpoint protection following the pandemic. Remote employees are the new normal and they are more likely than ever to use personal devices to connect to work networks. The pivot to remote work brought with...

Change The Game with KQL Workshop

Exploring Security Tabletop Exercises: A Cyber Concept Overview
Security Tabletop Exercises are an important form of organizational training and validation that can help mitigate the impact of cyber-attacks. Your business's Incident Response Plan serves as the blueprint that enables your team to detect, respond to, and...

What to Avoid When Pitching Cybersecurity to The Board
Effectively pitching cybersecurity to The Board is an essential role for all senior-level security team members. You may be presenting to Corporate Boards for many reasons —suggesting a new direction for the company security policy, explaining a complex...

How to Improve Your Cybersecurity Risk Management
A strong cybersecurity program is all about risk management. The most important question your business can ask is, “How can I mitigate risk? Cyber risks are business risks. Taking a risk-based approach to cybersecurity helps leaders balance cyber risks...

Webinar Recap: Pen Testing Your Defenses for a Stronger Security Posture
In a recent webinar, Difenda's cybersecurity experts discussed how you can overcome pen testing challenges and understand what exploitation techniques are possible in today's cybersecurity landscape. They covered why offensive security is important, the steps your...

Case Study: Building a Cybersecurity Program From The Ground Up
Overview The goal of any modern cybersecurity program is to streamline the people, process, and technology that drive an organization forward. This goal was clear for this large research company who had a lean staff but a lack of security processes. ...

5 Steps To Improve Your Company’s Risk Management
Cybersecurity is a complicated issue, which can't be solved quickly. But as intruders come knocking at your network door, your need for IT risk management and an effective cybersecurity strategy is more important now than ever before. Risk management, in general, is...

Derek Nugent: “all companies should measure and track their security posture“
Originally posted on Cybernews.com by the Cybernews Team. As security threats continually evolve, simplifying IT operations as a whole becomes more crucial than ever. Today, when cyber-attacks can no longer be stopped by antivirus software or firewalls, the...

New on Marketplace! Difenda AVM
We are thrilled to announce our ninth offer on Microsoft Marketplace: Difenda AVM. Making Difenda the leading MSSP in terms of breadth and depth of security services on Azure Marketplace, Difenda AVM effectively minimizes the window of opportunity for attackers...

A CISO’s Guide to Communicating Cybersecurity to The Board of Directors
You look in the mirror as you button up your shirt. Today's your presentation to the board and you need to make sure that when you leave that room the men and women around the table understand the cybersecurity strategy of the company. As Chief Information Security...

Not If But When: Difenda Knew Microsoft Would Outpace Competitors in Cybersecurity
We're thrilled to share that Gartner® Magic QuadrantTM named Microsoft as a leader for Security Information and Event Management (SIEM) and is positioned as the highest on Ability to Execute against competitors. The win celebrates...

Webinar: Pen Testing Your Defenses for a Stronger Security Posture
Access Webinar Pen Testing Your Defenses for a Stronger Security Posture Learn how you can overcome pen testing challenges and understand what exploitation techniques are possible in today's cybersecurity landscape. Plus, discover the steps your organization needs to...

A CISO’s Guide to Cybersecurity Management
As a CISO, your role is critical in today's cybersecurity landscape. Managing cybersecurity has become a top priority for organizations worldwide. While your main responsibilities will vary depending on your company's size and industry, you're ultimately responsible...

What is Managed Detection and Response? MDR Security Deep Dive
Businesses are increasingly targeted by cybercriminals attempting to steal confidential information and disrupt operations. These attempts include phishing scams, malware infections, ransomware attacks, and denial of service attacks. Managed Detection and Response...

Your Guide to Selecting an MDR Provider
Get Your Guide! Uncover The 6 Major Red Flags To Avoid When Selecting An MDR Provider In Your Guide to Selecting a Managed Detection and Response Provider you will also learn: - The top 5 things you must look for in an MDR provider - 3 current trends in the...

Gender Diversity: Going Beyond Recruitment, Promotion and Training
Addressing workplace gender inequality continues to be a pressing issue for all organizations, but especially those in the cybersecurity space. Many cybersecurity organizations are taking bold actions to address gender gaps in wages, recruitment and promotions by...

11 Cybersecurity Awareness Tips
Staying protected from cyberattacks is challenging. It's difficult to keep up when one click can cost your business millions of dollars. Ideally, everyone in your organization should be engaged in ongoing cybersecurity training, but in many cases, this is not...

Difenda is Leading the Race to Microsoft’s #1 MSSP
As we approach the launch of Microsoft's new partner program on October 1st, 2022, the race to Microsoft's number one Managed Security Service Provider (MSSP) has begun. Difenda's cutting-edge technical operations and commitment to cybersecurity expertise positions...

What is SOC-as-a-Service? Exploring Managed SOC Offerings
Network operations center, threat center, security operations center, whatever you call it, we all know that it's an integral part of our security operations. But, how exactly do they work and why do many organizations rely on SOC-as-a-Service as a valuable...

Difenda Build Partner Video

5 Things You Can Do Right Now to Reduce Cyber Risk For Your Business
As technological tools for blocking cyber-attacks online become more sophisticated cyber criminals are increasingly turning their attention to humans - the weakest link of every business's cybersecurity program. Meaning it is more important than ever to have...

Your Guide To Selecting A Vulnerability Management Provider
Get Your Guide! Your Guide To Selecting A Vulnerability Management Provider Here's what you will learn:- 5 things you should be searching for, - 5 red flags you need to avoid, and - Top trends in the industry you must know before you sign.

Top Three Tips for Cybersecurity in Education
Over the past few years, the education sector has become an increasingly popular target for malware and ransomware attacks. In fact, just in August 2022, over 80% of the world's malware attacks targeted organizations in the education sector1. The combined lack of...

Why Threat Detection is Only One Part of Maintaining Cybersecurity
In today's digital age, major security breaches are becoming more common every day. Are you sure your company is actually secure? Many organizations unknowingly operate in a state of breach. In fact, 54% of data breaches go undetected for an average of 168...

Difenda is Named One of MSSP Alert’s Top 250 MSSPs For 2022
We are thrilled to announce that Difenda has been ranked as one of the Top 250 MSSPs globally, for the second year in a row by MSSP Alert, a CyberRisk Alliance resource. The Top 250 MSSP list and research identify and honor the top MSSPs (managed security...

eBook: Communicating Cybersecurity in Uncertain Times
Download Your eBook! Communicating Cybersecurity in Uncertain Times In this eBook you will learn: - The top 5 points to highlight when making the case for cybersecurity in 2023. - What your Board of Directors needs to know when looking at security budgets for...

How This Pharmaceutical Organization Increased Visibility while Mitigating Risk with Difenda AVM
Overview Following a period of accelerated growth, this Pharmaceutical Organization experienced an increase in activity on their attack surface. At the time, they had many bespoke tools and apps causing an excess of vulnerabilities that their team was struggling to...

Vulnerability Management Best Practices
Vulnerabilities are discovered daily across all technologies. Multiply proliferating vulnerabilities across today's complex technological environments and you get a hamster wheel of never-ending risk. For years, vulnerability management has been a vital...

Reduce Data Loss From Phishing Attacks in Just Three Months with Difenda SAT
Overview Following an increase in security incidents targeting this Retail Company, they embarked on a fundamental IT strategic transformation including the restructuring of their end-user training program. At the time, the company's security awareness initiative...

eBook: Microsoft Sentinel Professional Services
Download Your eBook! Design, Implement and Deploy Microsoft Sentinel With Ease Whether you're deploying Sentinel from scratch, or just need a tune-up, Difenda can assist you with optimizing your Microsoft Sentinel environment. In this eBook, we outline the changing...

Maximize Microsoft Licensing and Implement Greater Controls with MDR for IT
Overview Like many businesses, this large energy manufacturer held a Microsoft Security E3 license but was unaware of what Microsoft products and services existed, which ones they were already paying for and which could help reach their business goals. To optimize the...

eBook: Microsoft Information Protection & Governance (IP & G)
Microsoft Information Protection & Governance Discover how to overcome common challenges and build an effective IP & G program that will better protect your data.

New on Marketplace! Microsoft IP & G
Data is today's most sought-after resource powering the global economy- making it the biggest target of unscrupulous attackers around the world. But your data is also at risk from employees using non-approved applications, unsecured devices, or accidentally sending...

What is SIEM as a Service? A Deep Dive into Managed SIEM
The reality is that cyber-attacks are a 24/7/365 threat to your business. A real-time threat monitoring program, such as a Security Information and Event Management (SIEM) system, that provides visibility into the network is now an essential layer of...

A Strategic Approach to Successful Penetration Testing
What is Penetration Testing? A penetration test is an assimilated hack conducted by highly qualified cybersecurity experts. It is a form of ethical hacking used to identify vulnerabilities within your environment. Penetration testing, also known as pen...

Case Study: Microsoft IP & G
Key Drivers & Business Outcomes Actively protecting data and information is a crucial activity for companies. Consolidating vendors and utilizing the tools you already have is a key step toward achieving this goal and one that many protection programs are lacking....

Case Study: Regaining Your Safety Posture After a Cyber Attack
Overview Following a collection of cyberattacks in the surrounding area, this city felt a sense of exposure and engaged with Difenda to optimize and strengthen its security posture. Like many organizations, this customer had already invested in Microsoft Security...

How Cloud Computing Improves Your Security Posture
Over the past decade, there has been a phenomenal shift of traditional security technology into cloud computing environments. Cloud-based servers like Microsoft Azure have transformed the way organizations are building IT infrastructure and protecting their data....

What is Endpoint Detection and Response?
Today's cybersecurity frameworks are inherently complex. With servers, printers, machinery and now remote computers and cellphones it has become difficult for organizations to create a unified approach to endpoint operations. From hiring qualified professionals to...

Webinar Recap: Cybersecurity in the Public Sector
The public sector has become a favored target for cybercriminals globally. Not only for their valuable data but because their legacy security is being outpaced by the technological evolution. Difenda understands that public sector organizations face unique...

Difenda’s End-to-End Microsoft Security Roadmap
Cybersecurity is inherently complex; its dynamic and spreads across a diverse array of systems and activities worldwide. Most businesses use dozens of security solutions and tools to manage their cybersecurity program. But, compiling so many tools into a...

eBook: End-to-End Microsoft Security Roadmap
Download Your eBook End-to-End Microsoft Security Roadmap Decipher the complexities of Microsoft Security and explore tailored guidelines for your company to do more with less.

Case Study: E2E Microsoft Security Roadmap
Key Drivers & Business Outcomes Utilizing the best cybersecurity tools and partners is important to ensure your security posture is up to date and in alignment with a specific framework. This was especially important for a large coffee manufacturer whose goal was...

The 10-Point Cybersecurity Checklist
Your security program encompasses all the people processes and technology that can be used to help you detect and mitigate threats. All these systems and elements can make it hard to know where to start when it comes to cybersecurity. We created this 10-point...

How does vulnerability management work?
You've likely heard of the importance of vulnerability management and cyber threat hunting. But do you know what these practices involve? When used together, you can be confident you're taking the necessary steps to develop a mature security plan. The terms...

Phishing prevention best practices
Have you ever clicked on an email that seemed legitimate, but wasn't? One-third of all cybersecurity breaches involve phishing; a common type of cyber-attack that you and your team should learn about in order to protect your organization. ...

How to implement a proactive security strategy
Proactive Cybersecurity | What it means for the public sector + best practices Government and healthcare organizations have copious amounts of personal data and account information that they are responsible for safeguarding. The abundance of valuable...

Case Study: Building a Proactive Security Program from Start to Finish
Overview Following an increase in activity on their attack surface, this Large Manufacturer was looking to establish a proactive security roadmap along with the appropriate government controls. The client was focused on updating and aligning their security program...

Video: MXDR for Operational Technology
Unified Threat Protection For All Your IoT/OT Devices MXDR for OT offers a turn-key agentless extended detection and response (XDR) that is rapidly deployed, works with diverse endpoints, IoT, OT, and industrial control system (ICS) devices. Watch our video below...

Difenda Earns Microsoft Threat Protection Advanced Specialization
We are thrilled to announce that Difenda earned our first Microsoft Advanced Specialization in Threat Protection. Threat protection represents a major initiative for Microsoft this year, and at Difenda we believe a proactive approach to threat detection...

Alert Fatigue Puts Your Organization at Risk; Here’s What to do about it
Originally featured in Cyber Defense Magazine. Read the article here. By Derek Nugent, Vice President Sales, Marketing & Customer Success at Difenda Alerts, notifications, and non-stop calls from shady telemarketers pitching extended warranties- we all get more...

Case Study: Gaining Visibility into the OT Environment
Overview Following a period of accelerated growth, this Pharmaceutical Organization experienced an increase in activity on their attack surface. At the time, they had many bespoke tools and were unaware of all the technologies in their OT environment. They needed a...

For the Second Consecutive Year, Difenda Wins Three Global InfoSec Awards
Read the release here. Difenda Wins Most Innovative Managed Detection and Response (MDR) Service Provider, Market Leader in Governance, Risk and Compliance (GRC) and Editor's Choice award for Vulnerability Management at the 10th Annual Global InfoSec Awards at...

Juliana Zaremba in Conversation with Cyber Defense Magazine Publisher Gary Miliefsky
Difenda Strategic Partnerships Director Juliana Zaremba was recently interviewed by Cyber Defense Magazine publisher Gary Miliefsky. Watch the video to hear Gary and Juliana talk about: ✅ What is SecOps-As-A-Service and how is Difenda different?...

How to choose a Microsoft MSSP
Two Businesswomen Using Laptop In Boardroom Meeting Your Certified Microsoft Security Partner must be able to help you detect and mitigate threats, meet regulatory requirements, while also helping you control costs through consolidation and automation. Most vendors...

Guide: The Ultimate Guide To Maximizing Microsoft Security ROI
Access Your Guide The Ultimate Guide To Maximizing Microsoft Security ROI Follow these proven steps to make the most of your Microsoft Security investment.

Case Study: Achieve A Truly Co-Managed and Collaborative Security Program
Overview Before engaging with Difenda this Large Manufacturer was struggling to gain visibility into their increasingly complex security network. At the time, their security solutions provider lacked the processes and sophisticated toolsets needed to provide this...
Video: Threat Actor Hunting, from IT to OT and Back with Microsoft and Difenda
Access Webinar Threat Actor Hunting From IT To OT And Back With Microsoft And Difenda Learn about our Microsoft-backed Difenda labs research and attack-driven approach to identify threat hunt criteria from IT to OT and beyond. Plus, see a real-time simulated attack...

Russia attacks Kyiv power grid with Industroyer2; new malware targets ICS networks
About the Threats A Russian-backed APT group used an updated version of Industroyer, dubbed Industroyer2, to penetrate a Ukrainian energy company in a failed effort to knock the Kyiv electric grid offline. The cyberattack, executed on April 8, 2022, was detected and...

Just Announced: MDR for OT now available on Azure Marketplace
For Immediate Release Difenda Shield Managed Detection and Response for Operational Technology is now available in the Microsoft Azure MarketplaceMicrosoft Azure customers worldwide now gain access to Difenda Shield Managed Detection and Response for Operational...

Microsoft Cyber Threat Intelligence Brief: Cyber Signals
Download Cyber Signals, a cyber threat intelligence brief informed by the latest Microsoft threat data and research Cyber Signals is a collection of insights from Microsoft's research and security teams on the frontlines, published in February 2022. This report...

Crown Corporation Achieves 100% Cybersecurity Cloud Adoption In 90 Days with MXDR
Key Drivers and Business Outcomes The goal of any modern cybersecurity program is to streamline the people, processes, and technology that drive an organization forward. For one Ontario-based retail Crown Corporation, realizing this goal required significant...

Case Study: Difenda MDR & Managed SIEM
Key Drivers and Business Outcomes Modern cybersecurity is focused on integrating the people, processes, and technology needed to help organizations evolve and thrive in the modern world. This company, a subsidiary of a large global parent organization, required...

How to keep data safe and secure
Every day it seems that the news is filled with stories about ransomware attacks and companies struggling to repair the damage brought about by the attackers. Across the globe and irregardless of the type of business, sensitive information is being leaked and the...
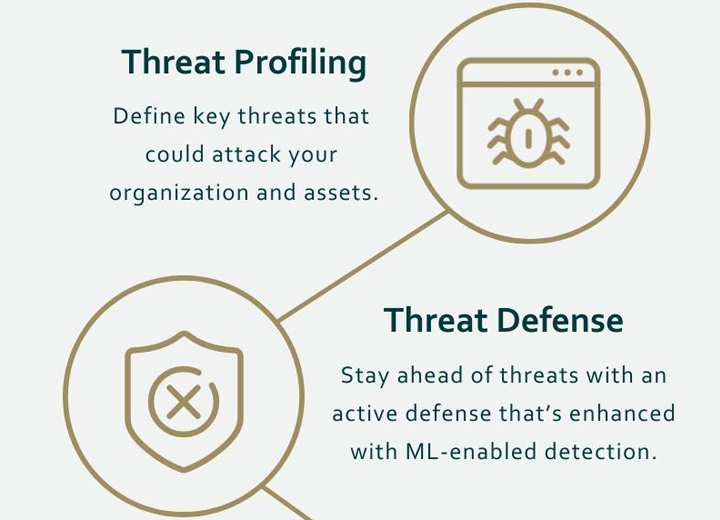
Infographic: 4-step MXDR Methodology to Provide Actionable Outcomes
Difenda's 4-step MXDR Methodology keeps your organization protected from all threats. We take an active approach using threat profiling, threat defense, threat hunting, and threat response to monitor day-to-day activity, identify advanced threats, and ensure your...

Women in Channel | Juliana Zaremba – Difenda
This post was originally published on ChannelTake.com Conversation with Juliana Zaremba | Director-Strategic Partnerships, Difenda Meet Juliana Zaremba. She is the newly appointed Strategic Partnerships Director at Difenda. As part...

Global cyberthreat advisory: Russia’s attack on Ukraine
About the Threat As part of Russia's attack on Ukraine, new data wiper malware, HermeticWiper, has infected hundreds of devices in Ukraine. Experts have predicted much larger cyberattacks from Russia than we are currently seeing, so this very well may be...

Women in Cybersecurity: The Emerging Game Changer
Perpetually on the cutting-edge, Difenda is committed to the “road not taken in a plethora of ways. And for a cybersecurity company in today's world, that means the promotion of gender diversity in a largely male-dominated culture, especially within the...

5 Key Takeaways: What’s Next in Security from Microsoft Digital Event
There is no doubt that cyber security is on the forefront of people's minds. From the very visible attacks on Ukraine's infrastructure, to businesses across the globe that are suffering at the hands of nefarious attackers, companies want to know that their data and...

Video: 5 Questions With Juliana Zaremba on Difenda’s Partner Program
https://vimeo.com/682918309 Tell us a little bit about you I'm Juliana Zaremba, Director of Strategic Partnerships at Difenda. I joined Difenda in January this year but I've worked with the organization for more than 5 years. I've been in the cybersecurity industry...

The High-Tech Gangsters of Organized Cyber Crime
Cyber criminals are banding together to share their areas of expertise and steal from and/or wreak havoc upon as many people and organizations as they can, either without regard for their victims or to intentionally inflict the maximum amount of damage possible. In a...

MDR Provider Difenda Launches Channel Partner Program, Appoints Channel Leader
MDR Provider Difenda Launches Channel Partner Program, Appoints Channel Leader Announcement Marks Company's Pivot to Channel-Led Growth GOODYEAR, Arizona- February 22, 2022- Managed Detection and Response (MDR) and SecOps-as-a-Service provider Difenda today...

Video: Difenda’s + Venafi Partnership
https://vimeo.com/539841186
Our New Website is Now Live!
https://vimeo.com/672077660 Difenda is pleased to announce that our new and improved website is live! We have made changes big and small in order to better serve your needs. As we continue on our mission to change the game in cybersecurity, we know how important it is...

Does Your Company Have A Cybersecurity Strategy?
When considering that corporations are likely to face a data security breach at some point, it becomes imperative that your company be prepared with a cybersecurity strategy. It may seem like a vexing challenge when the digital world is in constant flux—with the...

Video: Difenda + Venafi: Machine Identities
https://vimeo.com/539847238

Threat Advisory: Critical Apache Log4j Vulnerability
About the Threat On December 9th, the most critical zero-day exploit in recent years was discovered affecting most of the biggest enterprise companies impacting the Apache Log4j Java-based logging library. This vulnerability is also known as...

Top Cybersecurity Management Questions Answered
Cybersecurity management may seem complicated and, let's face it, it often is. But even without a degree in computer science, there are several important steps and processes you should have in place to ensure your IT infrastructure is protected from intruders. You...

How to Perform Successful Penetration Testing
Business, technology, internet and networking concept. Young businesswoman working on his laptop in the office, select the icon security on the virtual display. What is Penetration Testing? Penetration testing is known as an assimilated hack to identify...

What is alert fatigue?
What is alert fatigue in cybersecurity? Security teams are responsible for protecting an organization's data and systems from Cyberattacks. To do this, they rely on security tools that generate alerts when suspicious activity is detected. However, too many alerts can...

Video: Difenda Advanced Vulnerability Management | AVM
https://vimeo.com/551513528

Difenda Joins Microsoft Intelligent Security Association
Cybersecurity Provider to Join “Vibrant Security Ecosystem Oakville, ON, November 10th, 2021 — SecOps-as-a-Service provider and cybersecurity consultancy Difenda announced today that it has joined the Microsoft Intelligent Security Association (MISA). As...

The Beginner’s Guide to Cybersecurity Risks
Does the thought of cybersecurity threats keep you up at night? From one-person consultancies to multinational corporations, every business is at risk of a cyber attack. That's why all organizations—regardless of industry or size—need to strengthen their...

Managed Extended Detection & Response (MXDR) Video
https://vimeo.com/539822934?embedded=true&source=video_title&owner=138416541 #MicrosoftMarketplaceMDR
Video: Difenda Fireside Chat 2 – Azure Sentinel
https://vimeo.com/567042016
Video: Difenda Fireside Chat – Azure Sentinel – Rod Trent & Manoj Arora
https://vimeo.com/549461282

Why Microsoft Is Now the Leader in Endpoint Detection
The cybersecurity industry is no stranger to assumptions. It's the reason why the same established technology providers have been the focus for over a decade. It's also the reason why Microsoft was historically overlooked as a reliable solution provider in this...

Difenda is Co-Sell Ready – Microsoft Azure Marketplace
Bucharest, Romania - November 27, 2019: View of Microsoft Romania headquarters in City Gate Towers situated in Free Press Square, in Bucharest, Romania. TORONTO- Difenda Inc., a leading global managed security services provider (MSSP), is pleased to announce that two...

Making the Case for the Consolidated Security Stack: A Quick Overview
Whether you work as a chief information security officer (CISO) or just a cybersecurity specialist at the IT department, you know the difficulty of maintaining a secure and efficient network for your business. Threats of breaches, hacks, and other risks are...

Are Apologies from Cyber Criminals Enough? Are we Prepared?
Angry business man talking on phone disputing looking at laptop, stressed frustrated office worker arguing by mobile solving online computer problem with technical support complaining on bad service (Angry business man talking on phone disputing looki Author: Derek...

Difenda Wins the ‘Great Place to Work’ Award
We're proud to announce that Difenda has officially won the ‘Great Place to Work‘ award this year. Our recent win of this award is an achievement our entire staff holds close to our hearts, as it highlights our efforts to be a culturally sound, innovative, and...

Difenda Named to MSSP Alert’s Top 250 MSSPs List for 2021
Fifth-Annual List Honors Leading MSSP, MDR and SOCaaS Cybersecurity Companies Worldwide MSSP Alert, published by After Nines Inc., has named Difenda to the Top 250 MSSPs list for 2021 (https://www.msspalert.com/top250). The list and research identify and...

Kaseya Ransomware Attack and the Implications of Microsoft Defender for Endpoint (MDE)
By now, the story of the Kaseya ransomware attack is a cautionary tale to all MSP's and their clients. However, there's more to the story than meets the eye. Let's first examine the role Kaseya played in the attack. The Problem: Kaseya VSA is an on-premise solution...

What is a Compliance Audit?
Performing a compliance audit is a way to prove that the organization is compliant with regulatory and international standards and also measure how the organization's operations are regulated, risk-balanced, measurable, and can be monitored. Based on the results of an...
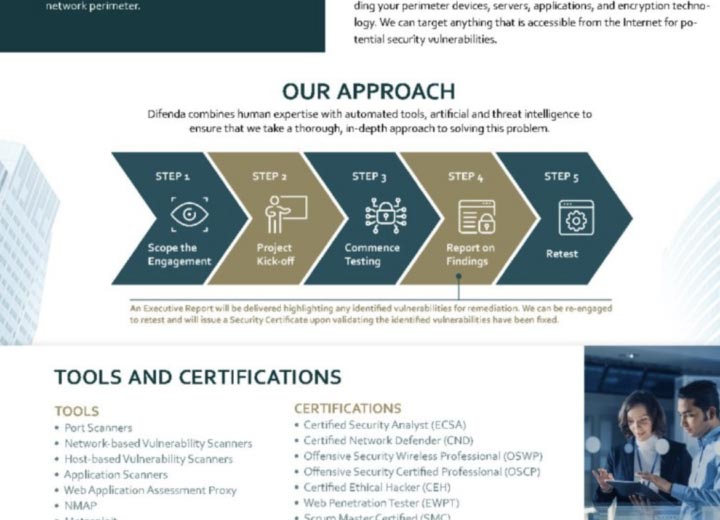
Product Brief: MDR for OT

How to Ensure Your Information is Safe with End-to-End Encryption
Every day, we hear news about new security breaches of personal information, credit card information, and sensitive data that was stolen or disclosed because it wasn't encrypted in transit or at rest. In today's multi-device working environment it is imperative to...

The growing need for cybersecurity risk management
Cyber security IT engineer working on protecting network against cyberattack from hackers on internet. Secure access for online privacy and personal data protection. Hands typing on keyboard and PCB Every organization with a digital footprint is a target for cyber...

5 Steps to Improve Your Company’s IT Risk Management
Young Female Government Employee Wearing Glasses Uses Tablet in System Control Center. In the Background Her Coworkers are at Their Workspaces with many Displays Showing Valuable Data. Cybersecurity is a complicated issue, which can't be solved quickly. But as...

Why organizations are consolidating security
In recent years, there has been an increasing trend toward consolidated security solutions. Instead of relying on multiple disparate tools, organizations are now seeking to have a single platform that can provide comprehensive protection. There are several reasons for...

What is the CIA Triangle and Why is it Important for Cybersecurity Management?
Confidentiality, integrity, and availability, aka the CIA triangle, is a security model created to guide information security policies within a company. The three elements of the CIA triangle are considered to be the three most important components of security. ...

Cybersecurity Advisory: CISCO Smart Install (SMI) Vulnerability
C3 Threat Advisory Reference# 04162018-1 Cisco has acknowledged the misuse of the Smart Install protocol on its network access layer switches running the IOS and IOS XE software leading to reports of the affected devices being reloaded causing network downtimes....

Cybersecurity Advisory: Password Spraying Attacks
Malicious cyber actors are increasingly using a style of brute force attack known as password spraying attacks against organizations in the United States and elsewhere. Brute-force attacks traditionally attempt to gain unauthorized access to a user...


