The line between inconspicuous routine actions and potential security threats is very thin. A mere click on an innocent-looking email can trigger a cascade of catastrophic events. For example, if an IT account gets compromised, and the breach escalates, it can infiltrate the customer’s Operational Technology (OT) environment and lead to operational outages, or worse.
This is a stark reality that many businesses confront daily. Security automation in the OT environment with Difenda’s Advanced Incident Response Orchestration (AIRO) engine is a game-changer. Its purpose is multifaceted:
- To save organizations time with security operations by automating triage and response actions, enriching incident telemetry, and
- Staying updated with the latest threat intelligence.
In this blog, we will detail Difenda MXDR for OT’s approach to triage and counteract threats within the OT Security environment with Difenda AIRO.
Threat Enrichment
On each security incident logged in Microsoft Sentinel, AIRO swings into action, operating at high speed to enrich incident entity information. Integrating with Microsoft Security technologies and other 3rd party API services, AIRO automates the process of gathering incident-related context, including IP addresses and URLs, to accelerate the triage process. These added insights and context are leveraged to guide further automated AIRO or C3 SOC triage and response actions.
Additionally, depending on the type of threat, Difenda AIRO can bridge the gap between IT and OT. It can correlate data from Defender for IoT with data from Microsoft 365 Defender. This enables us to find other anomalous activity from the same user.
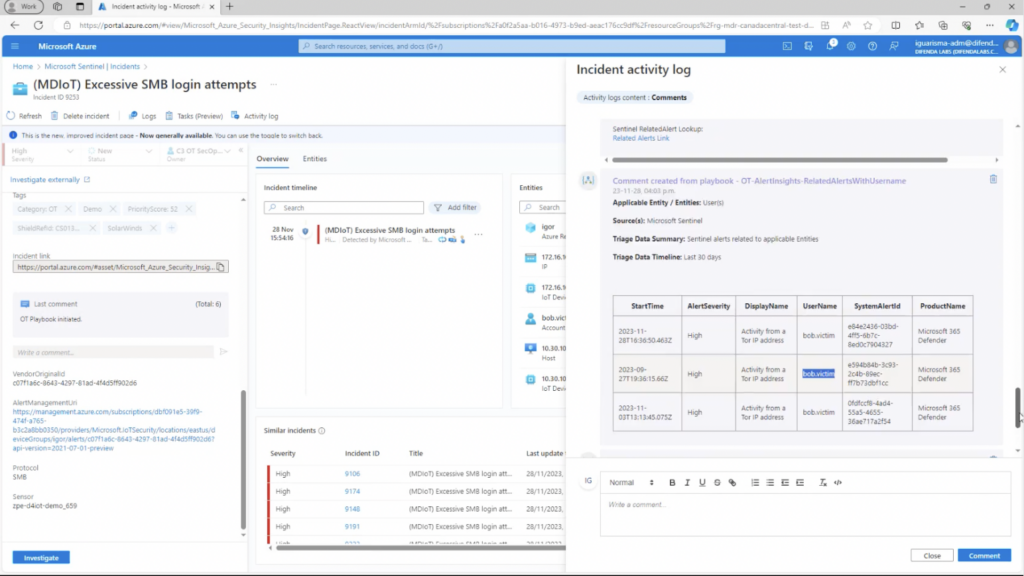
Automated Triage
AIRO’s versatility comes into play based on the nature of the incident, triggering additional triage playbooks for further enrichment. AIRO combines the insights obtained from the Threat Enrichment phase to identify benign or false-positive events automatically. For instance, in the event of an Account Compromise incident, AIRO will strategically trigger the relevant playbook.
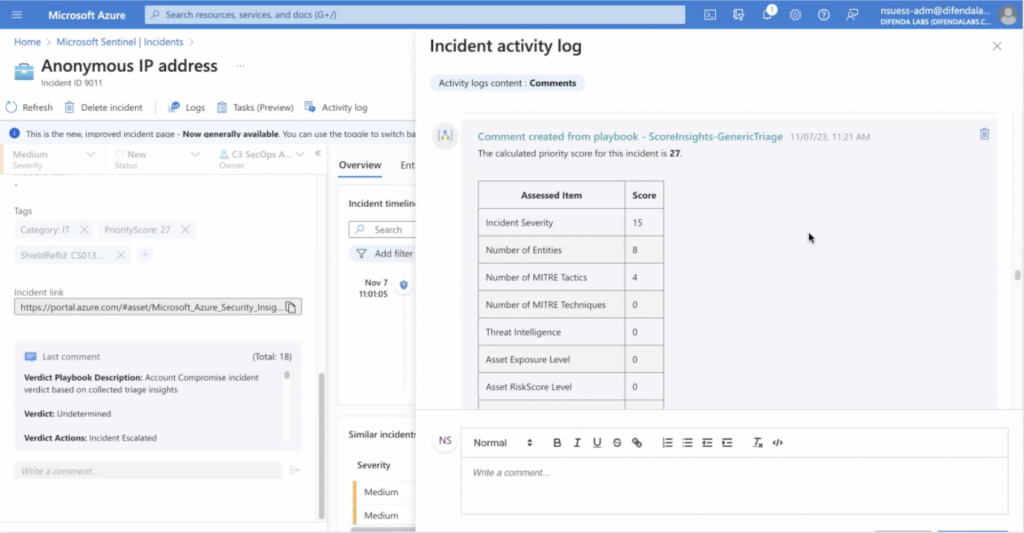
Incident Scoring
Once AIRO has executed all triage playbooks, the engine executes verdict playbooks. These determine if the incident is a false positive, true positive, or requires further review. The priority score is designed to assist with more fine-grained prioritization over traditional “High, Medium, Low” priorities.
AIRO assigns numeric scores to incidents based on the enrichment found in the incident triage phase and the business context you provided during threat profiling to help determine which alerts to look at and when.
Depending on the incident, additional triage playbooks may be called to provide further enrichment.
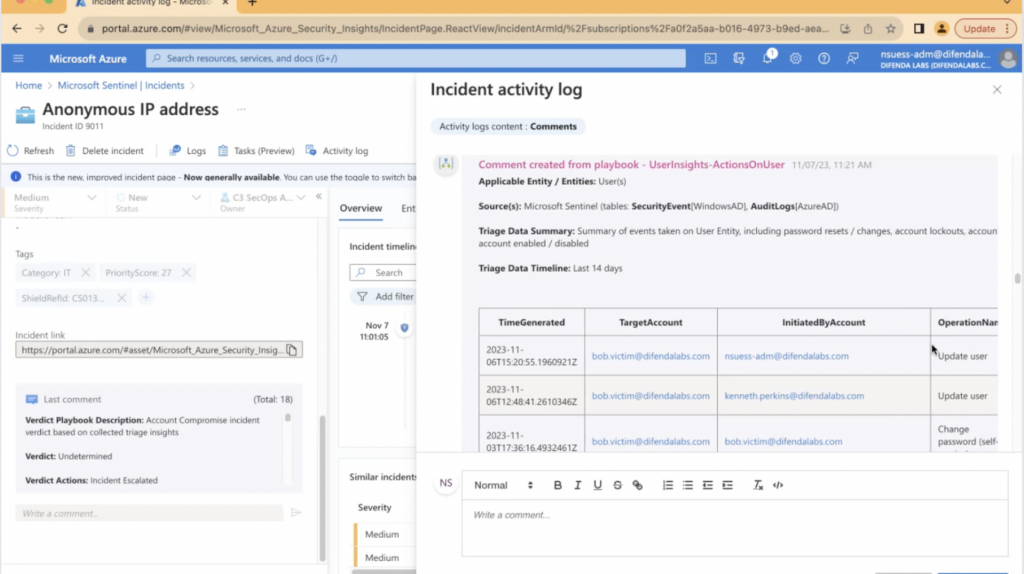
Bridging the Gap between IT and OT with Security Automation
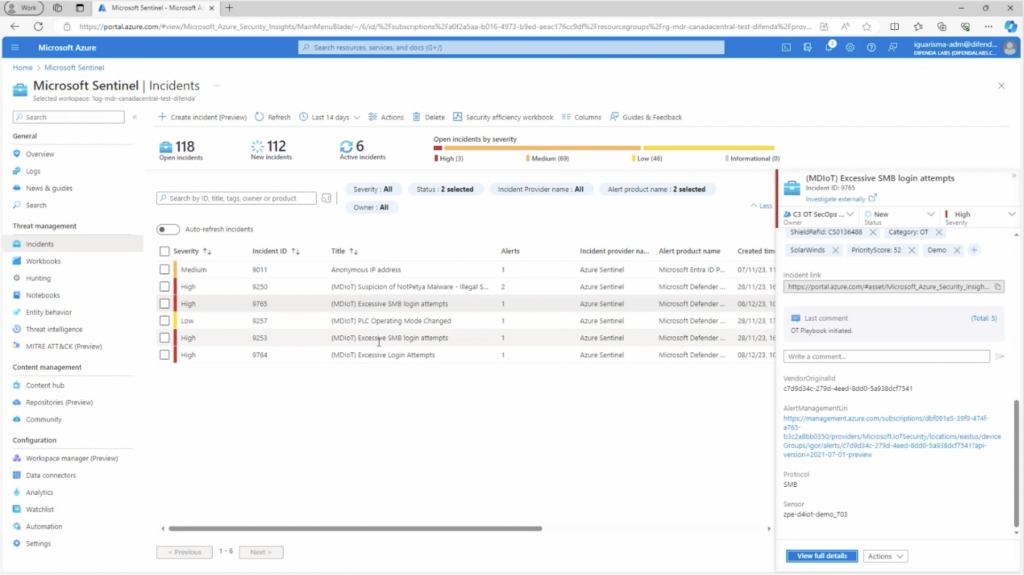
With Difenda’s strategic deployment and integration of both IT and OT security technologies, a custom Sentinel Dashboard can display both IT and OT data. This centralization of alerts into a single interface expedites our triage process and ramps up response efficiency.
AIRO goes beyond and correlates data from Defender for IoT with data from Microsoft 365 Defender to spot other anomalous activity from the same user. Instantly, it’s possible to see the user credentials used to gain access to the OT environment. More significantly, Difenda’s enrichment data verifies if there is a correlation of user data between attacks.
Difenda’s integrated Sentinel Portal and AIRO work in unison to provide greater visibility, highlighting all the environment alerts. In the case of any changes detected in the PLC’s operating mode, AIRO can automatically provide concise alert information that an analyst needs to make an informed decision and respond swiftly. AIRO also correlates data with alerts that are linked to the same device. For instance, if Defender for IoT detects an attempt of malware, AIRO will provide the details of this attempted breach.
Automated Response
With Difenda AIRO, the ability to respond effectively to an attack originating from the IT environment without disrupting operations in the OT environment is a reality. Depending on the incident, automated response measures can include revoking session access, disabling the affected account, or resetting the password in the IT environment, to stop a threat actor from compromising OT. Once the intruder is expelled, AIRO enables effective containment and management of the incident.
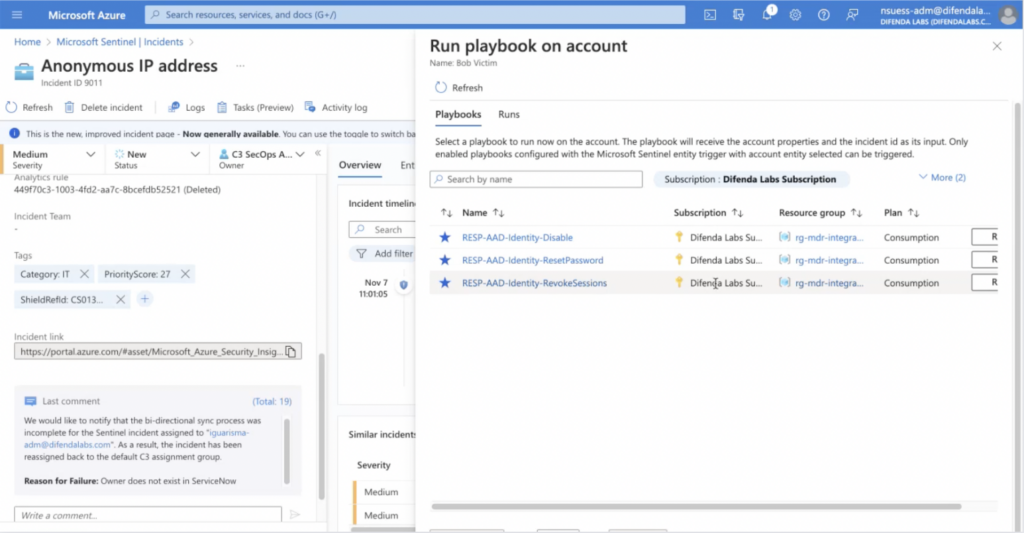
In essence, Difenda’s AIRO is not just a tool, but a comprehensive, adaptive, and proactive security automation solution to keep your Operational Technology Environment safe and secure.
SEE DIFENDA AIRO IN ACTION




