
Effective threat mitigation requires a deep understanding of the threat landscape and the context in which alerts occur. By analyzing and categorizing assets within the organization’s environment, cyber threat profiling offers insights into the potential impact of threats on specific assets and their relevance to the organization’s objectives.
Microsoft Defender for Endpoint’s Threat Intelligence, with its sophisticated analytical capabilities, proves to be an invaluable tool against the threat landscape. Difenda’s innovative threat profiling process leverages Microsoft Defender for Endpoint’s out-of-the-box capabilities to provide this critical context. We pair this with our insights to optimize automation and customization capabilities within your threat response process.
In this blog post, we explore Difenda’s threat profiling process and how it helps customers save time and harnesses the power of their existing Microsoft technology for improved cybersecurity.
Key Takeaways
- Threat profiling enhances cybersecurity by providing the business context needed to better protect your most critical assets.
- Difenda’s approach integrates seamlessly with Microsoft Defender for Endpoint, maximizing the use of your current security tools.
- Difenda’s threat profiling saves time through automation, offers clear guidelines for action, enhances interdepartmental collaboration, and safeguards critical data.
- Difenda adapts its services to meet your unique needs, ensuring you receive relevant and effective cybersecurity support.
- Difenda’s journey includes threat profiling, threat detection, threat hunting, and response- all designed to provide increasing value to its customers. Discover our 4-step methodology here.
What is Threat Profiling?
Difenda’s threat profiling combines a detailed analysis of threats that target an organization with a detailed classification of your business assets. It is a process of identifying contextually relevant business factors that might influence the outcome of a potential cyber-attack to specific assets.
This proactive measure frequently focuses on a specific cyber asset in an organization, like a system or application that requires protection. Within the realm of cybersecurity, threat profiles typically take into consideration factors like the personality and habits of the user. It may also include information on the motives, methods, and dedication of various cyber-criminals.
While Microsoft’s Threat Intelligence delivers insights about cyber threats, it becomes immensely more effective when paired with Difenda’s Threat Profiling. This proactive approach lends organizations a comprehensive view of their vulnerabilities and provides the information Difenda needs to respond to various threats on your behalf.
Leveraging Microsoft Defender for Endpoint
Difenda’s approach to threat profiling leverages Microsoft Defender for Endpoint’s capabilities out of the box. This means that organizations can harness the full potential of their existing security tools without the need for complex integrations or additional investments.
By working with Microsoft’s robust platform, Difenda ensures that its threat profiling process seamlessly integrates into the customer’s environment, making it accessible and efficient. This process reduced the amount of alerts your team encounters each day. Reducing alert fatigue by up to 70%.
How It Works
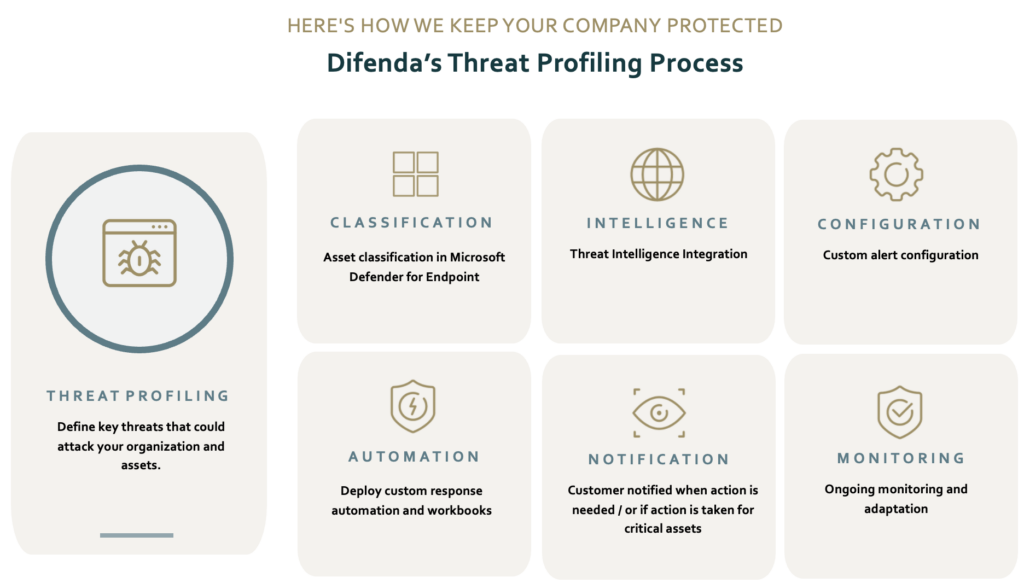
Difenda’s Threat Profiling Process
- Threat profiling enhances cybersecurity by providing the business context needed to better protect your most critical assets.
- Difenda’s approach integrates seamlessly with Microsoft Defender for Endpoint, maximizing the use of your current security tools.
- Difenda’s threat profiling saves time through automation, offers clear guidelines for action, enhances interdepartmental collaboration, and safeguards critical data.
- Difenda adapts its services to meet your unique needs, ensuring you receive relevant and effective cybersecurity support.
- Difenda’s journey includes threat profiling, threat detection, threat hunting, and response- all designed to provide increasing value to its customers. Discover our 4-step methodology here.
Leveraging Microsoft Defender for Endpoint
- Asset Classification: Difenda’s threat profiling process begins by ingesting your asset classification from Microsoft Defender for Endpoint. These classifications are based on the asset’s role and importance within the organization. This step involves categorizing assets into different groups, for instance critical systems, user workstations, servers, and data repositories. This classification process helps Difenda prioritize security efforts.
- Threat Intelligence Integration: Difenda continuously incorporates up-to-date threat intelligence into the threat profiling process. This intelligence includes information about emerging threats, malware signatures, and known vulnerabilities in the wild. By integrating threat intelligence feeds, Difenda ensures that threat profiling remains relevant and responsive to the evolving threat landscape.
- Custom Alert Configuration: Difenda’s threat profiling process allows for the customization of security alerts. Leveraging the asset classifications, risk assessments, and threat intelligence. Organizations can tailor their alerting mechanisms to their specific needs and priorities. This customization ensures that security teams are notified of the most critical issues and can respond promptly.
- Contextual Understanding: Threat profiling goes beyond simple alerts; it provides valuable contextual understanding. When an alert is triggered, security teams can access detailed information about the affected asset, its classification, associated risks, and relevant threat intelligence. This context empowers our security professionals to make informed decisions and take targeted actions.
- Ongoing Monitoring and Adaptation: Threat profiling is not a one-time process but a continuous and adaptive practice. Difenda’s solution continually monitors the IT environment and adjusts alert configurations in response to changing threats. This proactive approach ensures that security remains effective in the face of emerging risks.
- Reporting and Analysis: Difenda provides organizations with comprehensive reporting and analysis tools through the Difenda Shield. These tools offer insights into the effectiveness of security measures, the impact of threat profiling, and areas that may require further attention. The data-driven approach allows organizations to fine-tune their security strategies and allocate resources on their end more efficiently.
Benefits of Difenda Threat Profiling
- Time-Saving Automation: Automate asset classification, saving time and resources for other critical security tasks.
- Maximizing Efficiency: Optimize existing resources with Microsoft Defender for Endpoint, enhancing your cybersecurity posture.
- Clear Guidelines for Action: Establish a framework that outlines permissible actions, reducing the risk of missteps.
- Enhanced Interdepartmental Understanding: Foster collaboration among security, IT, and compliance teams for a cohesive cybersecurity strategy.
- Identifying and Protecting Crown Jewel Data: Pinpoint and safeguard your most critical data assets effectively.
Difenda’s Microsoft Threat Protection Advanced Specialization
The Threat Protection Advanced Specialization helps customers identify Microsoft partners with validated technical capabilities in deploying Microsoft Threat Protection, Microsoft Cloud App Security, or Microsoft Sentinel workloads.
To earn this specialization Difenda demonstrated our team’s skill and proved our expertise by displaying customer outcomes and showcasing how we protect customer environments against threats.
Learn more here.
Difenda’s Microsoft Threat Protection Advanced Specialization
The Threat Protection Advanced Specialization helps customers identify Microsoft partners with validated technical capabilities in deploying Microsoft Threat Protection, Microsoft Cloud App Security, or Microsoft Sentinel workloads.
To earn this specialization Difenda demonstrated our team’s skill and proved our expertise by displaying customer outcomes and showcasing how we protect customer environments against threats.
Meeting you wherever you are on your journey
At Difenda, we understand that every organization’s cybersecurity journey is unique, and we’re committed to providing contextual value at every step. Although we recognize that not all organizations have the same needs or face the same challenges with threat profiling, our customer-centric approach always starts out the same.
Through detailed reviewing and deeper conversations along the journey we customize our solutions to better align with your requirements. Perhaps more customization is needed, or maybe there’s a need for a more tailored approach to address your cybersecurity concerns.
This evolution of our services is part of our commitment to managed security. We aim to augment your cybersecurity capabilities throughout your entire journey with us because we understand that it’s not a one-size-fits-all situation. We start with a common foundation, but we’re always looking to refine and adapt our services based on the valuable feedback we receive from you.
Conclusion
Difenda’s threat profiling process is a game-changer in the realm of cybersecurity. By automating asset classification and harnessing the power of Microsoft Defender for Endpoint, it not only enhances security but also saves organizations valuable time.
This streamlined approach ensures that organizations can stay one step ahead of cyber threats while minimizing disruptions to their daily operations. With Difenda, customers can have confidence that their cybersecurity strategy is efficient, effective, and optimized to protect what matters most.
LET US HELP YOU BUILD YOUR BUSINESS CASE
Discover Our 4-Step MXDR Methodology


