In today’s world, technology is intertwined with nearly every aspect of our lives, and industrial operations is no exception. For cybersecurity leaders, understanding the key engines that monitor and detect Operational Technology (OT) security alerts is crucial.
In this blog post, we’ll delve into the five engines that drive Microsoft Defender for IoT alerts. Each engine serves a unique purpose, contributing to a comprehensive defense strategy tailored for the specific challenges of OT environments.
Key Takeaways
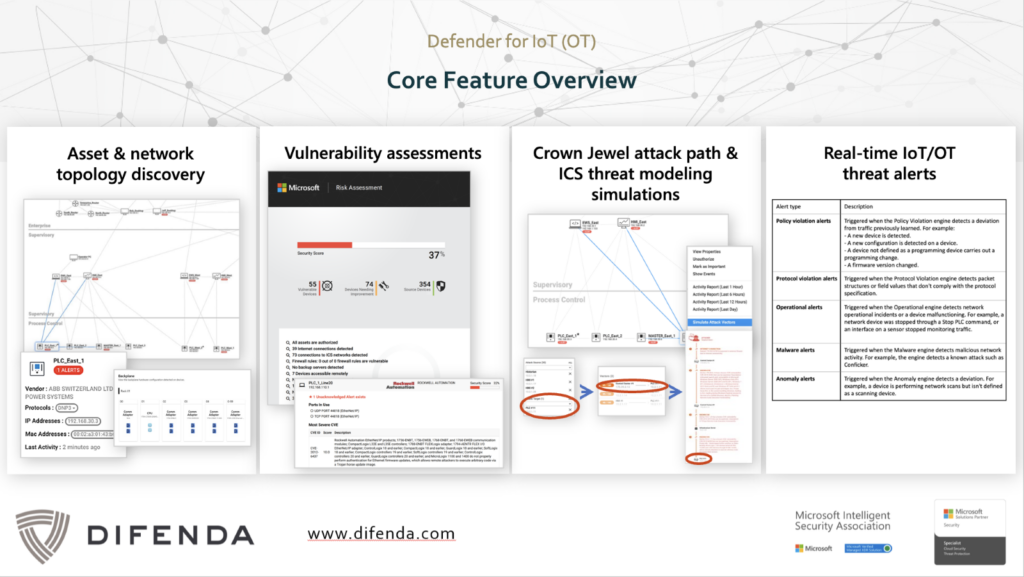
- Microsoft’s Defender for IoT employs five key engines to monitor different aspects of industrial protocol behavior.
- Policy Violation Alerts are triggered when a device behaves contrary to the predefined norms, enabling early detection of potential threats.
- Protocol Violation Alerts are raised when a device starts communicating abnormally, deviating from protocol specifications.
- Operational Alerts focus on the status of devices. If a crucial device goes offline, an alert is triggered, helping maintain smooth operations. These alerts are also useful in troubleshooting device issues.
- Malware Alerts detect the source of Malware threats and the affected devices based on IT and industrial malware.
- Anomaly Alerts are activated when unexpected behaviors occur, helping to identify and respond to sudden anomalies in device behavior.
- Automated triage and response processes within Sentinel, along with enrichment playbooks, reduce alert volume and provide a clear focus on threats.
- Difenda AIRO, integrated with Defender for IoT, uses automated enrichment playbooks and logic to provide critical information for incident investigations, minimizing duplicate alerts.
A Sophisticated Approach to OT Security
Microsoft’s Defender for IoT employs a sophisticated approach involving five key engines, each designed to monitor different aspects of industrial protocol behavior and trigger alerts when anomalies or policy violations are detected. This system provides the defense needed against both known and unknown threats, including those targeted at less common, ‘black box’ devices and protocols.
Policy Violation OT Security Alerts
The policy violation engine is designed to monitor the performance of well-understood industrial protocols. Deploying sensors strategically, the Defender for IoT passively monitors network traffic, creating a fingerprint of normal communications within the OT environment. Any deviation from this established norm triggers an alert. Defender for IoT is particularly adept at detecting anomalies, such as the introduction of new devices or unauthorized configuration changes, ensuring that unauthorized activities are flagged.
A good example of a scenario that would trigger a Policy Violation Alert is an encounter a controls engineer might have. Suppose they log into an engineering workstation and begin making changes to a Programmable Logic Controller (PLC). The traffic created by these setpoint changes to the low-level devices is something we would aim to capture because it could represent an unusual shift in communication patterns.
It’s important to note that Defender for IoT monitors on Layer 2 traffic according to the Purdue model. This includes PLC to PLC traffic and above.
Protocol Violation Alerts
Protocol Violation OT security Alerts come into play when a device begins to communicate in ways that deviate from the expected behavior of its assigned protocol – such as CIP or Modbus.
Consider the example of common industrial protocols like CIP or Modbus. Each of these protocols has a standard way of communication, a ‘norm’ that is expected. For instance, Modbus communication may have specified port ranges, data transfer rates, or flow patterns. When the communication does not conform, it raises a red flag in the system, triggering a Protocol Violation Alert. This mechanism is not reliant on learning your environment. It is based on metrics that cybersecurity solutions, like Microsoft Security, have established for various protocols.
These alerts provide a critical layer of defence against potential cyber threats exploiting protocol vulnerabilities within the OT infrastructure.
Operational Alerts
Operational Alerts, as the name suggests, are driven by the operational status of devices. They are particularly useful when dealing with network misconfigurations.
Consider a scenario where a device is not set up properly, perhaps due to inaccessible resources or other anomalies. This device will then operate in a peculiar manner, triggering operational alerts. Here’s another example: if a device, which usually checks in every 10 minutes, suddenly breaks the pattern, the system will generate an alert suspecting a disconnection. These alerts can be instrumental in troubleshooting devices. If a device goes down, the PCAP (packet capture) from the raised operational alert can be downloaded. This PCAP often contains invaluable information that can aid in diagnosing and rectifying the issue.
Malware Alerts
Defender for IoT’ Malware Alert engine operates much like traditional malware detection but with a crucial twist. In addition to IT threat intelligence, OT-related threat intelligence is added allowing it to identify industry-specific malware such as Stuxnet and NotPetya. This engine is equipped to pick up on communication patterns from compromised hosts or detect signatures of malicious code, providing a first line of defense against cyber threats.
The added advantage of Defender for IoT lies in its ability to understand and react to OT-related threats. The system can detect the source of the alert (e.g., an IT asset or an HMI) and the devices affected by it. By recognizing the specific communication patterns that these unique threats exhibit, the system is equipped to detect them early and respond promptly, mitigating potential damage. Correlating these alerts with other incidents helps paint a detailed picture of the threat.
See how Difenda AIRO used automation to correlate alerts between the IT and OT environment
Anomaly Alerts
Lastly, Anomaly Alerts are OT security alerts activated when unexpected behaviors occur within the system. These could be anything from unusual communication patterns to sudden spikes in data access. When a device, for example, starts “acting funky”, an anomaly alert is generated, offering an additional layer of protection.
In the realm of proprietary or less-known industrial protocols, the Anomaly Engine takes center stage. While it may not understand the specifics of every protocol, it excels at scrutinizing communication patterns. It raises alerts when a device behaves unexpectedly, providing a catch-all defence against potential threats lurking in the unknown.
Integration with Sentinel: From Alerts to Incidents
While Defender for IoT is a powerful security tool, it shines when integrated with an SIEM solution like Microsoft Sentinel. Combined with an SIEM it allows you to do incident correlation, grouping and more to provide added context to incident triage and speed incident response.
The Defender for IoT seamlessly integrates with Microsoft Sentinel, converting many alerts into actionable incidents. Understandably, not all alerts are equal. Some are not indicative of a compromise, serving only to correlate different aspects for an incident. Therefore, the system takes what could be an indicator of a compromise and triggers incidents based on that.
Where Difenda’s OT Security Operations stand out is our automated triage and response processes within Sentinel. Difenda AIRO groups incidents based on indicators of compromise, reducing the volume of alerts and providing a clear focus on potential threats. This integration streamlines incident response, allowing for a more efficient and targeted approach to cybersecurity within the OT environment.
For example, you could have one alert that is causing that issue and then 20 devices that are going offline. You don’t need to look at all 20 devices that are going offline as individual alerts. Difenda AIRO uses automated enrichment playbooks and logic that get more information that’s critical to incident investigations to group alerts. So instead of 20 alerts, you receive one.
Fortify your OT security posture for accelerated response
Remember, staying ahead in the world of OT security isn’t about reacting to every single alert. It’s about understanding the patterns, correlating incidents, and focusing on the alerts that matter.
Difenda MXDR for OT, stands as a vigilant guardian, powered by five engines that collectively fortify the OT security posture. As cyber threats continue to evolve, understanding and leveraging these engines become paramount in safeguarding critical infrastructure. The integration with Sentinel and Difenda AIRO ensures a swift and effective response. It turns alerts into actionable insights and enables organizations to stay one step ahead.
See Difenda MXDR for OT and Difenda AIRO in Action


