
As technological tools for blocking cyber-attacks online become more sophisticated cyber criminals are increasingly turning their attention to humans – the weakest link of every business’s cybersecurity program. Meaning it is more important than ever to have an alert and well-trained staff that are actively looking to reduce cyber risk.
However, armed with the proper tools and knowledge, employees can transform security from weakness into strength. Here are five ways you can help reduce cyber risk:
1. Update your software
Skipping or delaying software updates on your computer or phone is something we have all done. But by doing so we are keeping the door open for threat actors to access our private information, putting us at risk for identity theft, fraud, and more. In fact, many of the most harmful malware attacks are often utilizing software vulnerabilities that can already be patched with current updates. So instead of procrastinating your software updates, prioritize the few minutes it takes to reduce cyber risk and be safer online.
2. Enable two-factor authentication where possible
Many cybercriminals are actively buying password data online to get access to your accounts. Two-factor authentication adds a second layer of protection to your password-protected accounts and devices. This additional layer of defense makes it harder for cybercriminals to gain access to your accounts and steal your data. Today, some malware attacks called spyware can actively be recording everything you type on your device and send it back to malicious cybercriminals. However, it is a lot harder for them to track an authentication app or facial recognition tools.
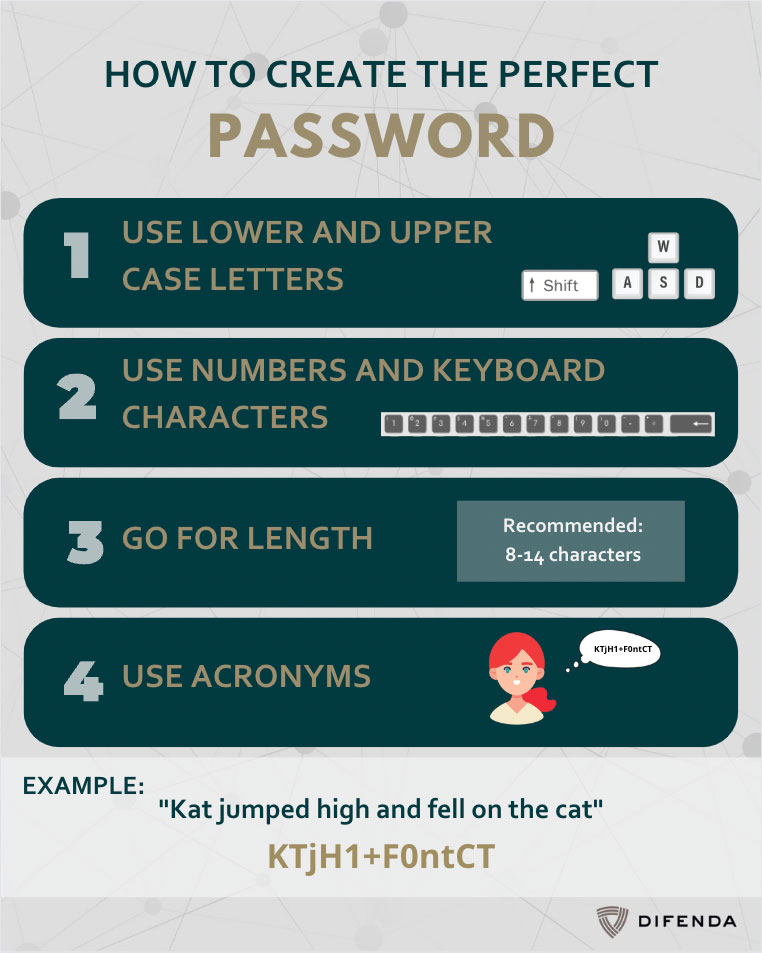
3. Use stronger passwords
When two-factor authentication is not possible, using stronger passwords, and unique passwords for different accounts can help reduce cyber risk. The stronger your passwords are in terms of length and variation of characters, the more protected you are from threat actors and malware attacks. Additionally, you want to use different passwords for each account because if a threat actor does get access to one of your passwords, you want to ensure they do not have access to all of your personal data access a variety of platforms.
4. Learn how to recognize phishing attacks
One-third of all cybersecurity breaches involve phishing. To fight phishing scams, you need to be aware of the threats, such as the possibility of bogus emails in your inbox and malicious links on social media. Be suspicious of any unknown links and never open unsolicited attachments. Arm yourself with the right tools to spot and prevent phishing attacks with these six tips.
5. Verify requests for personal information – even on “trusted websites and apps
If you receive a request for personal information online, don’t visit the links implanted in the email or message. Instead, visit the website directly from a new tab and update or provide the information from there. Even if a request looks like it is coming from a trusted source, it is always better to visit the site first and verify that the information was requested or is necessary.
If you would like to know more about what you can do to reduce cyber risk and stay safe from cyber criminals online read our 11 tips for cybersecurity awareness blog.


