You may have recently heard rumors that Microsoft Security added IoT capabilities to their E5 licensing structure. This is exciting because Defender for IoT has long been a separate licensing technology. With OT devices likely to double by 2030 this could have a large impact on risk mitigation for companies with limited security budgets.
Well, it’s true! Microsoft security is now including a limited number of enterprise IoT (eIoT) devices to their E3 and E5 licensing capabilities. So, while you may not be able to leverage the complete power of Defender for IoT with your existing licensing, you can streamline business processes and eliminate critical blind spots by discovering unmanaged eIoT devices.
In this post we’ll define the type of devices this new offer covers, what you can accomplish with this new technology and how you can start maximizing these new capabilities.
Key Takeaways
- Defender for IoT is now accessible for customers under Microsoft 365 E5 and E5 Security plans, with each eligible user encompassing coverage for up to five enterprise IoT (eIoT) devices.
- eIoT devices are enterprise-grade IoT devices designed for corporate use. Including smart thermostats, edge servers, gateways, and edge routers.
- The incorporation of eIoT security in these plans increases network visibility, reduces security blind spots, and strengthens threat detection.
- Microsoft’s E5 centralizes security operations by integrating personnel, skill sets, and technologies. This streamlining reduces the need for cross-training and specialists in multiple areas.
- Deploying Microsoft Defender for Identity and Microsoft Defender for Endpoint enables an enhanced level of incident correlation, improved visibility, robust protection against threats and a more efficient security system.
- Get Started with a PoC today.
Updated Licensing Overview: What changed?
Microsoft transitioned its Defender for IoT technology to a per device per month licensing structure as a component of Microsoft 365. Therefore, Defender for IoT is now accessible for customers under Microsoft 365 E5 and E5 Security plans.
Each eligible user license now encompasses coverage for up to five enterprise IoT (eIoT) devices without extra costs.
Read the Official Microsoft Announcement
The Difference Between IT, OT, IoT and eIoT
In the realm of cybersecurity, the distinction between IT, OT, IoT, and eIoT is crucial.
- IT is concerned with data and information systems, including personal computers, printers, software applications ect.
- OT is the hardware and software used to change physical state in industrial control and automation systems.
- Examples: Industrial Control Systems (ICS), SCADA (Supervisory Control and Data Acquisition) systems, PLCs (Programmable Logic Controllers), DCS (Distributed Control Systems), smart sensors in manufacturing plants, and robotic systems used in production.
- IoT represents a network of physical devices, vehicles, home appliances, and other objects embedded with sensors and software that enable them to connect and exchange data.
- Examples: Smart thermostats, fitness trackers, smart home devices (smart lights, smart locks, smart cameras), connected cars, wearable health monitors, and industrial IoT devices like connected machinery and equipment in smart factories.
- eIoT simply refers to enterprise-grade IoT devices designed for corporate use.
- Examples: Smart thermostats, Edge servers, gateways, and edge routers.
It is important to note that the updates to Microsoft E3 and E5 licenses only include eIoT devices.
Benefits of eIoT Security in Microsoft 365 E5 and E5 Security plans
The incorporation of eIoT security in Microsoft 365 E5 and E5 security plans offers a plethora of advantages to customers. One of the primary benefits is increased network visibility, empowering businesses to identify and manage previously unmanaged eIoT devices. This feature significantly reduces security blind spots, ensuring comprehensive coverage of the enterprise IoT device landscape.
Moreover, it strengthens threat detection by pinpointing potential vulnerabilities in the system, thereby bolstering the overall cybersecurity stance. Continuous monitoring of the eIoT device estate helps identify abnormalities swiftly, enabling rapid response to security incidents.
By combining Microsoft’s E5 licensing model with eIoT security Microsoft enables businesses to better protect their operations in an increasingly digitized and connected world.
The role of Microsoft’s E5 in enabling centralization
Microsoft’s E5 plays a pivotal role in centralizing security operations, integrating personnel, skill sets, and technologies to strengthen your organization’s defense stance. It reduces the need for cross-training and eliminates the need for specialists in multiple areas, thereby streamlining your security operations.
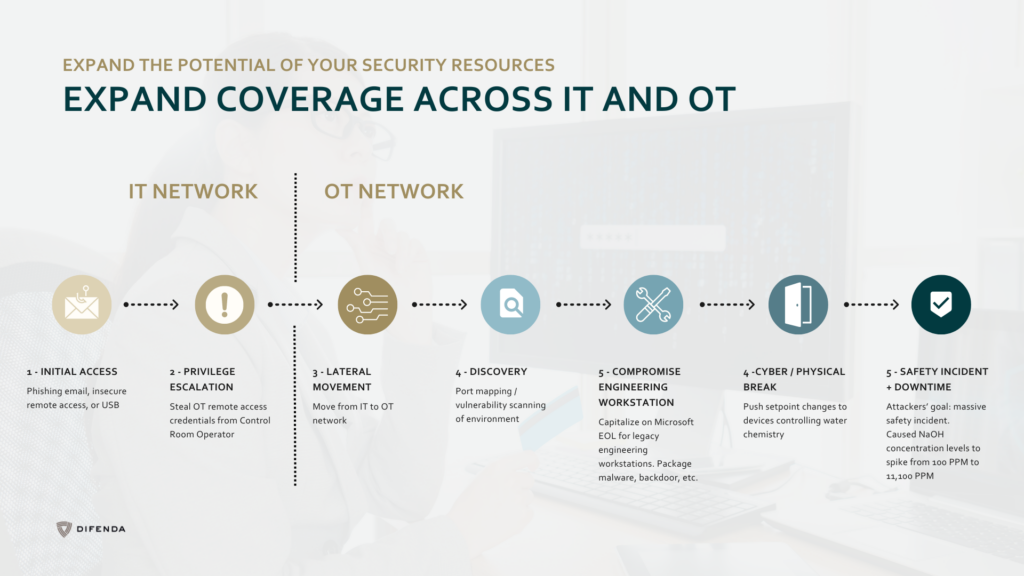
The main benefits of Microsoft E5 for OT security are the deployment of Microsoft Sentinel, Microsoft Defender for Endpoint (MDE) and Microsoft Defender for Identity (MDI).
Microsoft Defender for Identity is particularly useful for companies whose operational technology (OT) infrastructure maintains a separate domain controller. Or has unique identity and access management protocols. It allows the collection of crucial data related to user activity, enabling an enhanced level of incident correlation. Furthermore, Microsoft Defender for Identity provides visibility and controls by tying back security events to user activity.
Additionally, deploying Microsoft Defender for Endpoint agents can significantly enhance the security posture of manufacturing companies. MDE enables us to access rich asset and event details to aid in incident investigations that D4IoT fires. This provides robust protection against sophisticated threats, offering behavioral-based detection, and providing an automated investigation and response system. This results in a more streamlined and efficient security system, reducing the burden on security teams.
By leveraging the capabilities of Microsoft’s E5 licensing on top of Defender for IoT, manufacturing companies can benefit from improved threat detection, enhanced incident correlation, and a more efficient, streamlined security operation.
Get Started with Microsoft Defender for IoT today!


