C3 Threat Advisory Reference# 04162018-1

Cisco has acknowledged the misuse of the Smart Install protocol on its network access layer switches running the IOS and IOS XE software leading to reports of the affected devices being reloaded causing network downtimes. Cisco subsequently released advisories addressing vulnerabilities in this feature, which if exploited, give the ability to a remote attacker to trigger the reload of the affected device, causing a Denial of Service (DoS). The attacker may also be able to execute arbitrary code on the device.
Overview
Cisco Smart Install is a feature that offers zero-touch deployment for new devices using “plug-and-play configuration and image management. Using this feature, a customer can ship the Cisco device to any location, install and power it on without any additional configuration. The Smart Install feature stays enabled on the device after its deployment and since it does not use any authentication mechanisms by design, it leaves the device susceptible to this attack.
The vulnerability currently affects devices which have the “Client role within the Smart Install configuration. Devices with the “Director role are not affected as confirmed by Cisco. This advisory is rated Critical and the vulnerabilities are identified with the following IDs: CVE-2018-0171 and CVE-2018-0156.
Exploit Details
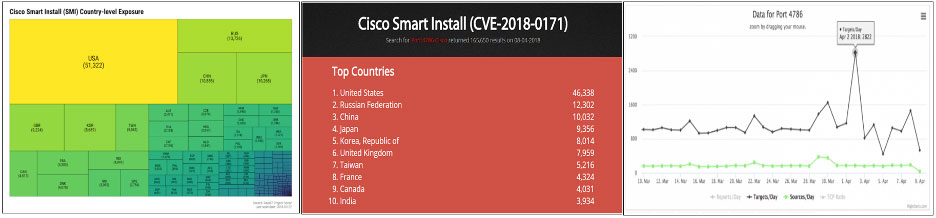
The vulnerability is exploited due to improper validation of packet data which can be accepted by a vulnerable device since this feature does not require any authentication. When an attacker sends a crafted Smart Install message to a device listening on port TCP 4786, which if successful, could lead to a buffer overflow on the device that may eventually cause an indefinite loop resulting in a watchdog crash or a reload of the device.
The Smart Install Exploitation Tool (SIET) is readily available on the internet making the exploit of this vulnerability more accessible to script kiddies or threat actors. A recent scan on the internet revealed more than 4000 vulnerable devices in Canada that may be susceptible to this attack.
Impact
A successful exploitation of this vulnerability may have the following impact:
- Change the TFTP server address on the device to a TFTP destination server that may be controlled by the attacker.
- Copy the device’s startup-config to the said TFTP server.
- Replace the existing startup-config with the attacker’s version of the startup-config file.
- Upgrade the IOS image on the device with the one propagated by the attacker.
- Execute high-privileged configuration mode CLI commands on the device.
- Reboot and reload the device, which may reset the device to the factory default configuration.
- Execute arbitrary code on the device.
- Cause an indefinite loop on the device triggering a watchdog crash.
- Disrupt regular operations and business services.
- Financial losses due to unavailability of network resources.
- Potential harm to an organization’s reputation.
Identification
Cisco has released the Cisco IOS Software Checker on its official page so that network administrators and users can enter their Cisco device software IOS release version to check if they are affected by this vulnerability. Alternately, the following commands on a Cisco device can ascertain the status of the Smart Install feature:
- Switch1# show vstack config
- Check the role of the device; if it’s “Client, then the device may be susceptible.
- Switch1# show version
- Copy the firmware version of the Cisco IOS or IOS XE software and paste it on the Cisco IOS Software Checker to confirm if the device is vulnerable or not.
Mitigation or Remediation Actions by Organizations
There are no workarounds to address this vulnerability. The following options are available to network administrators:
Customers who do not use the Smart Install feature:
- Disable the feature using the “no vstack configuration command on the device.
Customers who use the Smart Install feature only for zero-touch deployment:
- Once the zero-touch installation is complete, disable the Smart Install feature using the “no vstack configuration command on the device.
- Propagate this command on all devices deployed using this feature.
- Add this command to the IOS configuration which is pushed on each Smart Install Client as part of the zero-touch deployment.
- If the “no vstack command is not supported by the IOS, apply access lists (ACLs) on client switches to block traffic on port TCP 4786.
Customers who use Smart Install feature for management beyond the zero-touch deployment:
- Apply access lists (ACLs) to allow only the Smart Install “Director to send traffic to the Smart Install “Client switches on port TCP 4786.
- Block any other traffic on this port from all IPs on the client switches.
- Apply these access lists on all interfaces.
Customers can also block traffic on port TCP 4786 on the network firewalls.
Customers can detect the use of SMI on Cisco devices using the following command:
- alert tcp any any -> any 4786 (msg:”Smart Install Protocol”; flow:established,only_stream; content:”|00 00 00 01 00 00 00 01|”; offset:0; depth:8; fast_pattern;)
Customers can also detect the use of SIET on Cisco devices using the following command:
- alert tcp any any -> any 4786 (msg: “SmartInstallExploitationTool_GetConfig”; flow: established; content:”|00 00 00 01 00 00 00 01 00 00 00 08 00 00 04 08|”; offset:0; depth:16; fast_pattern; content:”copy|20|”;)
- alert tcp any any -> any 4786 (msg:”SmartInstallExploitationTool_ChangeConfig”; flow:established; content:”|00 00 00 01 00 00 00 01 00 00 00 03 00 00 01 28|”; offset:0; depth:16; fast_pattern; content:”://”;)
Actions by Difenda
- The Cyber Command Team at Difenda has put together specialized use cases to detect the use of SIET or SMI for the clients forwarding relevant logs to us.
- Additionally, periodic reports are being executed to check the traffic details on port TCP 4786.
- For the clients for whom Difenda offers firewall device management services, the said port has been added to the block list for traffic originating from the internet and the firewall threat signatures have been updated.
References
- US-Cert Advisory Alert (TA18-106A)
- Cisco Advisory CVE-2018-0171 (Critical)
- Cisco Advisory CVE-2018-0156 (High)
- Cisco PSIRT Advisory
- Cisco Smart Install Configuration Guide
- Hacker News Advisory
- SANS Advisory
- Rapid7 Advisory


